money
money
InfoSpace
money
Cheapstuff
money
Adfirmative
money
dSide Marketing
money
Netaxle
money
eWoss
money
AdOn Network
money
Trafficsolar
Screenshots - Trafficsolar Spyware, Long Chain of Intermediaries, InfoSpace Running Google Conversion-Inflation Click Fraud
Google Click Fraud Inflates Conversion Rates and Tricks Advertisers into Overpaying - Ben Edelman
This page gives screenshots showing on-screen displays as traffic flowed from Trafficsolar spyware through intermediaries and on to Google and finally back to the site my Automatic Spyware Advertising Tester had initially requsted, Finishline.com. All testing occurred on December 31, 2009.
See also discussion in main article, as well as a packet log and video.
The Targeted Web Site: Continental
My AutoTester began browsing at Finishline.com, a popular online shoe store, on a virtual computer infected with Trafficsolar spyware (among other advertising software, all installed through security exploits without user consent). (Screenshot taken from video at 0:08.)
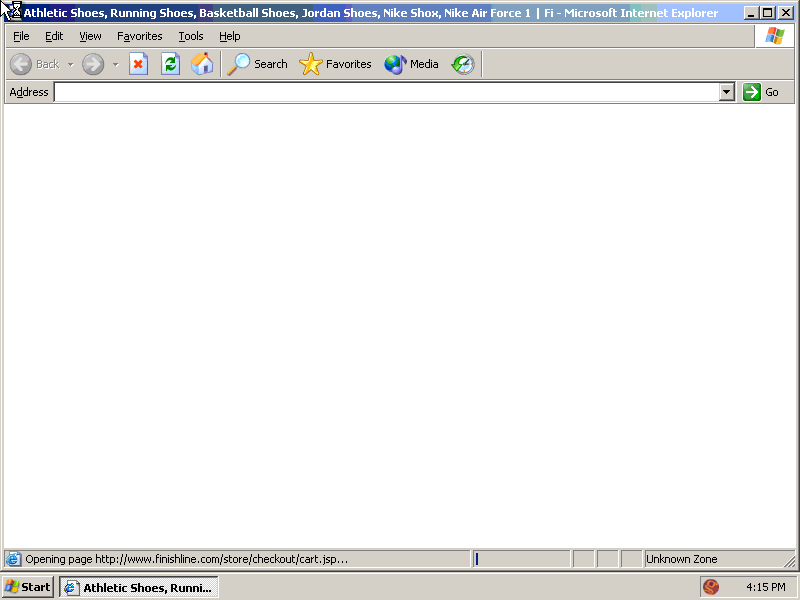
Trafficsolar spyware opened this full-screen unlabeled popup. (Screenshot taken from video at 0:10.)
Although the popup shows Netaxle, the packet log confirms that traffic reached Netaxle via AdOn and eWoss. This is entirely expected: Many redirect steps do not manifest themselves in visible browser displays.
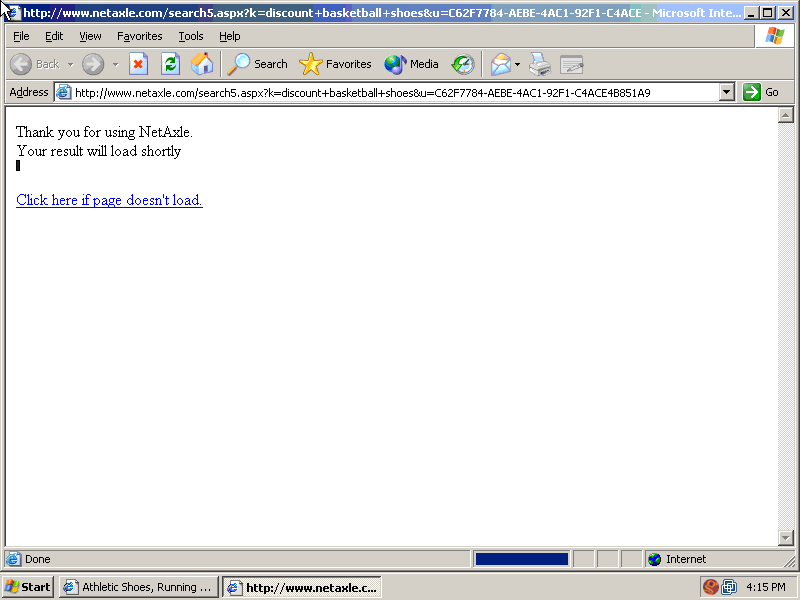
The Next Visible Redirect Step: Cheapstuff
The next visible redirect step showed Cheapstuff, as pictured here. (Screenshot taken from video at 0:13.)
Here again, the packet log usefully details all intermediaries -- namely, that traffic flowed from Netaxle to dSide Marketing to Adfirmative to Cheapstuff.
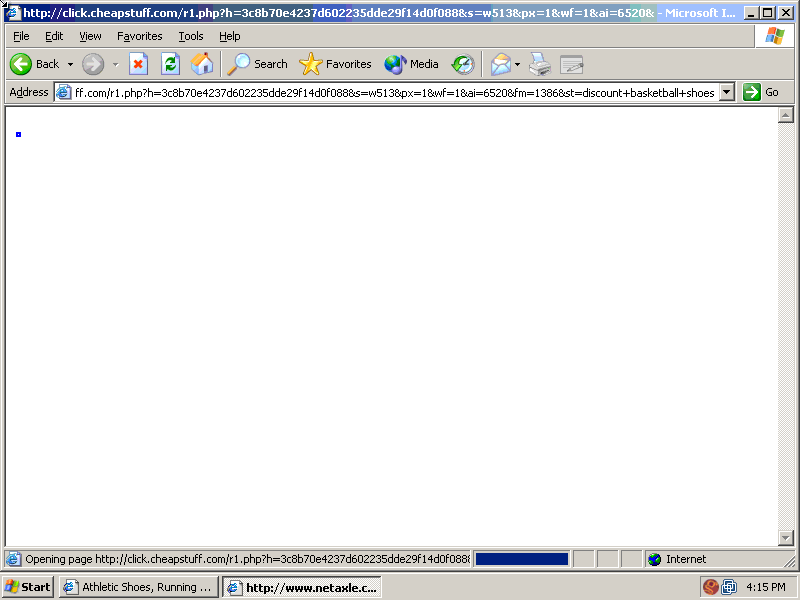
The Final Visible Redirect Step: InfoSpace to Google
Two second later (video at 0:15), Cheapstuff had begun to redirect to InfoSpace. Notice the browser's Status Bar (bottom of screen), referencing InfoSpace as the next redirect step.
The full InfoSpace URL is truncated, showing only the beginning of the rawURL= parameter that gives the next step in the redirect chain. But the packet log confirms the full URL -- a Google /aclk ("ad click") link. The truncated status bar text shows a portion of the letter "g" in Google.
Unfortunately, this is the end of the useful portion of my video of this incident. After the image shown above, another popup covered the entire on-screen display -- preventing further video confirmation of what occurred. Because the video was prepared by my Automatic Spyware Advertising Tester, there was no one present to close the popup and visually demonstrate the results of this click fraud. the That said, the packet log confirms traffic flowing through to Google's /aclk "ad click" link, then onwards to Finish Line, the victim advertiser.