I ought to be a Vonage enthusiast. I support Vonage’s efforts to protect network neutrality. I applaud their flexible voice over IP service and their efforts to compete with incumbent phone companies. I’m even a VoIP customer (albeit using a competitor’s service).
But instead of praising Vonage, I have to criticize them — not for their core business, nor for their customer service (which others have repeatedly criticized), but for their reckless advertising practices. Vonage spends huge amounts on advertising — more than $20 million per month. (source) Unfortunately, among this spending is widespread and substantial spyware-delivered advertising.
For years, my manual and automated testing have documented Vonage ads appearing in all the major spyware programs. Now that Vonage has completed its IPO — itself promoted as a way to raise more money to buy more advertising — this page presents twelve recent examples of Vonage ads appearing in spyware.
| Spyware-Delivered Pop-Up Ads | Banners Injected Into Others’ Sites | Spyware Lead Acquisitions | Spyware-Delivered Banner Farms |
| Direct Revenue
Targetsaver – covering AOL Targetsaver – covering a sexually-explicit site SearchingBooth |
Fullcontext – ad injected into Google.com
Searchingbooth – ad injected into True.com Searchingbooth – ad injected into eBay DollarRevenue – replacing an ad within Boston.com |
Direct Revenue – Vendare’s Myphonebillsavings
Direct Revenue – NextClick’s Phonebillsolution |
Hula’s Global-Store
ExitExchange |
Vonage’s Spyware-Delivered Pop-Up Ads
 A Vonage Ad Shown by Direct Revenue
A Vonage Ad Shown by Direct Revenue
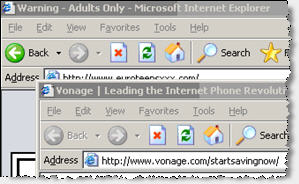 A Vonage Ad Shown by Targetsaver
A Vonage Ad Shown by Targetsaver
money
Traffic Marketplace
money
Targetsaver
The Money Trail – How Vonage Pays Targetsaver
I have repeatedly observed Vonage buying “ordinary” spyware pop-up ads from vendors like 180solutions, Direct Revenue, and eXact Advertising. See e.g. the top thumbnail at right, a March 2006 screenshot of a Vonage ad appearing through Direct Revenue. See also my March 2005 report of Vonage ads appearing through eXact Advertising. These relationships add up to big money: BusinessWeek last week reported that Vonage paid Direct Revenue $31,570 in a single month of 2005 — a remarkable $110 for each customer Direct Revenue sent to Vonage. Meanwhile, in its litigation against Intermix, the New York Attorney General specifically documented Vonage’s ads appearing in Intermix KeenValue pop-ups.
Beyond notorious spyware such as Direct Revenue and Intermix, Vonage ads also appear through less well-known spyware, including through programs that continue to be installed onto users’ computers through security exploits (without user consent). The second thumbnail at right shows a Vonage ad shown by Targetsaver (a California maker of software that becomes installed without consent, tracks users’ behavior, and shows targeted pop-up ads). Targetsaver sends traffic to Vonage in the way set out in the diagram at right: Targetsaver sends users to Traffic Marketplace which forwards users to Vonage (via aQuantive / Atlas, which serves to track most Vonage advertising purchases).
http://a.targetsaver.com/adshow
http://www.targetsaver.com/redirect.php?clientID=…&finalURL=…
http://www.targetsaver.com/js/jf1.html
http://ad.trafficmp.com/tmpad/banner/ad/tmp.asp?poID=emwG
http://t.trafficmp.com/p.t/i15275/37389831/
http://clk.atdmt.com/VON/go/trffevon0740000126von/direct/01/
http://www.vonage.com/startsavingnow
Despite the word “target” in its name, Targetsaver isn’t particularly picky about where it shows Vonage’s ads. The screenshot at right reflects a Vonage ad shown while a user tries to sign up for AOL — perhaps reasonable targeting, in that both companies provide telecommunication services. But Targetsaver also shows Vonage’s ads in unseemly locations, such as when users browse sexually-explicit sites. Screenshot.
Vonage pop-up ads also appear through various other spyware. Additional examples: Vonage shown in a SearchingBooth pop-up (via Rpowermedia and Traffic Marketplace), Vonage shown in a Dollar Revenue pop-up (via Oridian / Cydoor, Yield Manager, Falk eSolutions AG / DoubleClick, and Traffic Marketplace).
Spyware Injections of Vonage Ads – Into Others’ Sites
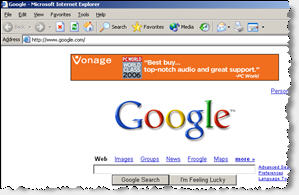 Fullcontext Injecting a Vonage Ad into Google
Fullcontext Injecting a Vonage Ad into Google
money
Yield Manager
money
MediaPrecision
money
Fullcontext
How Vonage Pays Fullcontext
As users revolt against pop-up ads, a growing trend is to inject ads into others’ sites. Users who receive injected ads may not notice they’re infected with spyware; the telltale signs are, perhaps, less obvious than extra pop-ups. And by hooking into Internet Explorer’s API, injection isn’t particularly difficult.
Of course ad injection raises serious legal concerns. A spyware vendor probably infringes a site’s copyright by inserting an ad right into that site — all the more so when such insertion occurs without a user’s consent and when such insertion lacks any labeling or disclaimer. But consider the vendors who use these methods: they already face substantial legal liability, e.g. from their nonconsensual installations of spyware onto users’ computers. Such vendors are unlikely to be deterred by possible copyright liability.
Despite the problems with spyware-injected banner ads, I have repeatedly observed Vonage ads appearing through banners injected into others’ sites using spyware, without permission from those sites. In general, the resulting Vonage banners appear in places where, but for the spyware at issue, no banner would exist. Consider e.g. the Google screenshot at right. The “real” Google site does not include a banner above the Google logo. Although the banner appears to be an integral part of Google’s site, the banner was injected into the site’s on-screen display by Fullcontext spyware; it was not placed there by Google.
The left and center screenshots below show similar ad injections by Searchingbooth. True.com and eBay do not sell ads that appear above their respective sites. Instead, the Vonage ads at issue were injected there by Searchingbooth, yielding the on-screen appearances shown below.
The DollarRevenue example, right screenshot below, shows a special kind of banner injection. Whereas the first three examples inject ads above a site (albeit within the site’s own window), DollarRevenue injects its ads into a site — covering a banner placed by the site (which would yield payment to the site) with a banner for DollarRevenue (which produces payments to DollarRevenue). This business model is not altogether novel; Claria (then Gator) pioneered this approach with its 2001 covering of other sites’ banners. But whereas Claria quickly abandoned this practice, in the face of IAB and other criticism, DollarRevenue continues unabated. For a particularly vivid view of DollarRevenue’s ad replacement, see the video of this ad injection. Notice the original Boston.com ad appearing for a fifth of a second at 0:00:3.65, only to be covered nearly instantly by the DollarRevenue-injected Vonage ad.
Vonage pays the respective spyware vendors through the relationships set out in the diagrams below and at right. Click an ad thumbnail for a full-size image, along with a packet log of associated network transmissions.
 Searchingbooth Injecting a Vonage Ad into True.com Vonage
money Traffic Marketplace money Adecn money Rpowermedia money Searchingbooth How Vonage Pays Searchingbooth |
 SearchingBooth Injecting a Vonage Ad into eBay Vonage
money Traffic Marketplace money Rpowermedia money Searchingbooth How Vonage Pays Searchingbooth |
 Initial Boston.com Ad – Visible for Only 0.2 Seconds – video
Vonage
money 24/7 RealMedia money Yield Manager money Oridian (Cydoor) money DollarRevenue How Vonage Pays DollarRevenue |
The ads at issue were injected by DollarRevenue (apparently located in the Netherlands), Fullcontext (purportedly of Anguilla), Searchingbooth (from Deskwizz, giving an address in Quebec, Canada).
Vonage Lead Acquisitions via Spyware Pop-Ups
 Vendare Group Using Direct Revenue to Promote Vonage
Vendare Group Using Direct Revenue to Promote Vonage
money
Vendare Group / eMarketMakers
money
LeadClick Media / eAdvertising
money
Rextopia
money
RevenueLoop
money
Direct Revenue
The Money Trail – How Vonage Pays Direct Revenue
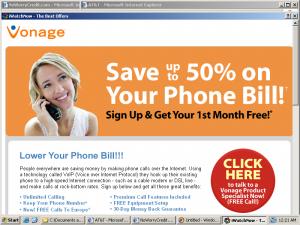
As recently as March 2006, I was still observing Vonage ads shown by notorious spyware vendor Direct Revenue. (Screenshot.) But Vonage partners continue to advertise with Direct Revenue — even using Vonage-supplied site designs to do so. So Vonage’s money still reaches Direct Revenue and still helps to fund Direct Revenue.
Consider the top screenshot at right. As I browsed other telecom sites, I got a pop-up promoting Vonage. The pop-up is nearly full-screen — covering all but the title bars of the pages I had requested. The pop-up ad lacks a visible URL, but packet log analysis indicates that it was loaded from www.myphonebillsavings.com. Notably, the bottom of www.myphonebillsavings.com reads “©2001-2006, Vonage Marketing, Inc.” — reflecting that this Vonage-branded page was, by all indications, designed by Vonage itself.
To see who placed this pop-up with Direct Revenue, I again turn to packet log analysis. I observe that loading the ad entailed loading the following URLs. Click the list for the full packet log.
http://xadsj.offeroptimizer.com/imp/servlet/ImpServe?urlContext=http%3A%2F%2F…
http://login.revenueloop.com/sw/3211/CD1087/
http://rextopia.com/sw/5551/CD436/1087%3A%3A3211%3A%3A%3A%3A%3A%3A18a259ac88a…
http://www.eajmp.com/sw/7601/CD154/
http://clicks.emarketmakers.com/redir.aspx?id=671651&AFFID=CD154
http://clicks.emarketmakers.com/redir.aspx?from_pu=true&id=671651
http://clk.atdmt.com/VON/go/thvndvon0550000019von/direct/01?bannerid=671651&f…
http://www.myphonebillsavings.com/?bannerid=671651&AFFID=CD154
This analysis indicates that traffic and money flowed as listed at right. RevenueLoop (a California-based ad network), or a RevenueLoop business partner, bought traffic from Direct Revenue (controlling server offeroptimizer.com). Then RevenueLoop sent traffic to Rextopia (a New Jersey affiliate network), which redirected to Eajmp.com (LeadClick Media’s eAdvertising, of California), which redirected to eMarketMakers, which redirected to aQuantive’s Atlas and finally on to Myphonebillsavings.
The last few links of this chain reflect substantial involvement of Vendare Group. Vendare owns eMarketMakers, and Whois data indicates that Myphonebillsavings is also registered to Vendare Group. But despite receiving venture funding from Insight Venture Partners, Vendare’s ties to spyware are well-known. For example, I have widely observed — and carefully documented — Vendare’s New.net installed through security exploits without users’ consent . Furthermore, Vendare’s eMarketMakers directly funds a variety of spyware. For example, in January 2006 I documented eMarketMakers promoting NetZero using traffic purchased directly from 180solutions, and in March 2005 I documented eMarketMakers promoting Earthlink and Petchews via traffic purchased directly from eXact Advertising. Despite the direct and well-documented relationships between Vendare and spyware, Vonage nonetheless purchases advertising from Vendare and its eMarketMakers group.
Vendare’s Myphonebillsavings is just one of many Vonage partners still paying to receive traffic from Direct Revenue. Last month I also observed Phonebillsolution pop-ups appearing through Direct Revenue. Like Myphonebillsavings.com, Phonebillsolution.com’s copyright line reflects creation by Vonage. Phonebillsolutions hides its Whois data, but directly requesting the IP address of the Phonebillsolution web server yields a default page titled “NextClick Media” (a California-based ad network). The final thumbnail at right shows NextClick promoting Vonage using Direct Revenue.
Spyware-Delivered Banner Farms Promoting Vonage
 Look2me and Hula’s Global-Store Promoting Vonage
Look2me and Hula’s Global-Store Promoting Vonage
money
ad networks (one or more)
money
banner farm
money
placement intermediaries (zero or more)
money
spyware vendors
How Vonage Funds Spyware via Banner Farms
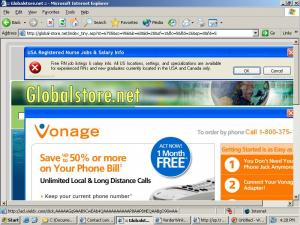
Last month I explained the problem of spyware-delivered banner farms: Web sites that buy spyware traffic (directly or indirectly), then show substantially only ads, thereby serving as ad placement intermediaries. I posted three distinct examples of Vonage appearing in spyware-delivered banner farms: Hula’s Global-Store promoting Vonage in a large window at screen center, a further Global-Store promotion of Vonage in a smaller window partially covered by another ad, and in ExitExchange.
But there are plenty of other banner farms, and in my testing most banner farms promote Vonage. For example, my June banner farm article mentions Whatsnewreport, which I have also observed promoting Vonage.
The diagram at right reflects the canonical relationships between Vonage, ad networks, banner farms, and spyware
Vonage’s Spyware Advertising in Context
Vonage isn’t the only advertiser with widespread spyware ad-buys. Other buyers of untargeted or semi-targeted ads get plenty of spyware-delivered advertising too. For example, I see Verizon ads in spyware pop-ups with remarkable frequency. In a future article, I’ll present screenshots of some other big spyware advertisers.
As best I can tell, Vonage does not specifically intend to have its ads shown in spyware. Instead, the advertising chains shown above reveal that these are generally indirect relationships, not direct spyware ad buys. (In comparison, see my September 2005 report of Expedia directly and intentionally buying spyware-delivered advertising from numerous notorious spyware vendors — a practice that, to its credit, Expedia subsequently stopped.) Yet by failing to take appropriate precautions and failing to diligently supervising its ads, Vonage makes payments to spyware vendors — funding spyware that is known to harm users’ PCs.
Vonage may seek to write off these examples as insignificant within its nine-digit advertising budget. But these spyware placements have important negative externalities: When Vonage pays spyware vendors, even indirectly, Vonage helps make spyware more profitable, and helps make the spyware problem worse. Even if Vonage is content to waste some money on buying unwanted spyware ads, it still needs to take action to avoid funding software that damages users’ PCs.
When asked about Vonage’s spyware funding, Vonage CEO Jeffrey Citron last year told the Associated Press “We do everything we can to make sure our partners adhere to our standards.” I disagree. There’s plenty more Vonage could do. For example, Vonage could refuse to work with partners like Vendare, that have known ties to spyware vendors and that even make and distribute their own spyware. Vonage could refuse to work with Traffic Marketplace and Yield Manager — partners that can’t provide reasonable assurances of keeping ads out of spyware. Vonage could specifically review all its advertising partners, and Vonage could prevent those partners from subcontracting with further unverified subpartners of their own. Vonage may consider these changes burdensome or inconvenient. But based on current practices, Vonage can’t credibly claim to be doing “everything” to stop spyware advertising. To the contrary, as the many examples above indicate, far more work is still required.
Last month Vonage won an “Effie” award for the “effectiveness” of its advertising campaign. I can’t speak to Effie’s criteria in granting this award. But advertisers might appropriately hesitate to praise an advertising strategy that, whether intentionally or recklessly, includes buying ads in spyware.
Beyond Vonage, criticism might reasonably focus on the advertising intermediaries that broker Vonage’s spyware placements. For example, Vonage receives and tracks all these spyware placements through aQuantive’s Atlas advertising. Atlas’s Acceptable Use Policy proclaims that “Atlas technology may not be used in connection with any downloadable application that is downloaded without notice and consent.” But I see no indication that Atlas actually enforces this policy: All the programs discussed above are programs I have observed installed without consent, yet these placements repeatedly flow through Atlas, as shown in each posted packet log. Other ad intermediaries lack even Atlas’s anti-spyware statement: Searching 24/7 Real Media’s site for “spyware” yields no hits, and 24/7’s lengthy and prominent code of conduct does not prohibit use of spyware.As advertising service providers, advertising specialists, publicly-traded companies, and purported ethical leaders, aQuantive, 24/7, and others could do far more to keep spyware out of their networks.