Yesterday Governor Schwarzenegger signed into law SB 1436 (“Computer Spyware”), a California bill that speaks to certain programs installed on users’ computers. The bill admittedly speaks to programs that trick users, harm users, and take advantage of users. So why don’t I support it?
SB1436 prohibits a number of activities. It bans, for example, transmitting computer viruses from a users’ computers (22947.3(a)(1)), using a computer as part of a denial of service attack ((a)(3)), and presenting an option to decline installation of software when selecting that option will in fact cause software to be installed nonetheless ((c)(1)). These are surely bad actions. But they’re all prohibited under existing law — fraud, unfair trade practice, computer fraud and abuse act, etc. When investigators, lawyers, and researchers have tracked down bad actors using these methods in the past, they’ve proceeded with suit, with considerable success. (See e.g. Melissa virus writer’s jail sentence.) So we don’t need SB1436 to address these outrageous activities.
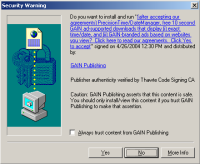 A Claria drive-by download prompt — allowing the user to press ‘Yes’ and have software installed, without first seeing Claria’s license agreement.
A Claria drive-by download prompt — allowing the user to press ‘Yes’ and have software installed, without first seeing Claria’s license agreement.
In contrast, SB1436 fails to speak to the truly controversial activities — many of them arguably “borderline” — that have actually been used by major players in the spyware space, whose installed user counts now reach into the tens of millions. Consider Claria’s 5,500 word license agreement. As presented in Kazaa’s installer (screenshots), Claria’s license is 20% longer than the US Constitution, and it requires 56 on-screen pages to view in full. Or, consider Claria’s drive-by installer (screenshot), where a user can press “Yes” without ever even seeing Claria’s license. More recently, Claria’s drive-bys have begun to show users the Claria license — but only after the user presses Yes, and only after the software is installed! What should we make of such installation practices? Has a user really “accepted” Claria’s software when the user receives unhelpful, confusing, and/or untimely disclosures? Even if the user is a minor? Even if the user mistakenly thought Claria’s software was necessary to view the web page that triggered the drive-by? Some courts may think that pressing “Yes” indicates assent — no matter the circumstances, no matter how one-sided the terms presented, and for that matter even if the terms weren’t actually presented (but were merely linked to). But I don’t think that’s a necessary conclusion, given the length and presentation of the supposed agreement.
SB1436 had an opportunity to address these deceptive installation tactics by clarifying standards for notice and consent. Indeed, the first draft of SB1436 (dated February 19, 2004) addressed Claria’s tactics directly: “‘Spyware’ means an executable program that automatically … transmits to the provider … data regarding computer usage, including … which Internet sites are or have been visited by a user” — exactly what Claria does. The February draft went on to set out various requirements and disclosure duties, even including a minimum font size for disclosure. That’s not to say the February bill was perfect — certainly there was more fine-tuning to be done. But it sought to establish disclosure duties for all companies transmitting information about users’ online browsing — not just a few outrageous outliers who send viruses.
Unfortunately, SB1436’s initial comprehensive approach somehow got lost between the February draft and the August revisions. A recent RedHerring article claims the bill was “gutted” by “the well-heeled and influential online advertising lobby.” Claria’s chief privacy officer recently stated that he had “met with the staffs of members who have proposed legislation” — though not mentioning any special efforts to modify the bill. Whatever Claria’s role, even a quick reading shows that the revised bill won’t affect Claria’s current practices.
Meanwhile, Claria gets to go on record not only supporting the law, but perhaps even complying with it from its first day in effect. Claria can now claim the implicit endorsement of California law: After all, if California passed a spyware law, and Claria complies, then (the logic goes) Claria must be a legitimate business that consumers and advertisers should happily do business with. But the truth is not so simple: Claria’s deceptive installation methods continue, tricking tens of millions of users into receiving Claria software without truly understanding what they’re getting into.
A better spyware bill would address the subtleties of Claria’s methods — would address lengthy, confusing licenses, and licenses shown only after supposed consent. Interestingly, some of the pending federal legislation speaks to disclosure requirements for programs like Claria. The federal bills are far from perfect. But they at least seek to address the harms, like Claria, that actually plague millions of users day in and day out. More on the proposed federal legislation next month.