My last few posts have all covered spyware revenue sources (e.g. major advertisers, pay-per-click ads, and affiliate networks). But I always come back to poor installation practices as the core of the spyware problem. And nonconsensual installations continue to benefit surprisingly large vendors. Today’s focus: New.net.
Introduction to New.net
New.net provides a proprietary domain name system that allows it to sell nonstandard domain names to advertisers. These proprietary domains are resolved through New.net’s own servers, so these domains are accessible only to users whose ISPs have chosen to support New.net (few have), or to users with New.net’s client software installed on their PCs.
Despite major funding from Idealab, New.net hasn’t made a lot of friends. When New.net first announced its navigation DNS experts criticized New.net for breaking the namespace: In a New.net world, not all computers can reach all domain names. Internetnews called New.net an “end-run around ICANN,” and Internet Society staff worried of New.net causing “address collisions” by creating new domains that already exist elsewhere.
Facing so much criticism, New.net understandably sought to improve its image. But rather than changing its unpopular practices, New.net instead tried to silence its critics. In 2003, New.net sued Lavasoft, claiming false advertising and trade libel when Lavasoft detected New.net’s software and offered users an easy way to remove it. This wasn’t a clear win for New.net: Some of its claims were dismissed under anti-SLAPP rules, and in January 2005 New.net voluntarily dismissed its pending appeals. Then again, Lavasoft’s August 2004 change log reports removing signatures for New.net — suggesting that Lavasoft changed its classification of New.net to avoid further litigation. My Threats Against Spyware Critics table also reports New.net threats against CounterExploitation.
New.net’s Installation Practices — And an Example Nonconsensual Installation
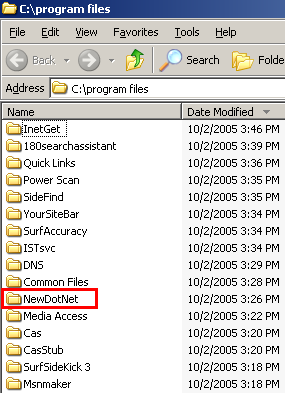 A partial listing of programs installed via the Pacimedia exploit.
A partial listing of programs installed via the Pacimedia exploit.
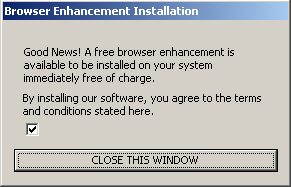
The Pacimedia exploit’s first screen. Notice no disclosure of specific programs to be installed. Notice no terms or conditions actually provided. Installation proceeds if a user presses “close this window” — without requiring that the user affirmatively indicate consent.
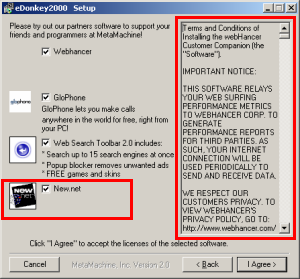 Another misleading New.net install — disclosed via a one-word on-screen description (“New.net”) without any explanation of function, purpose, or effect. Finding the New.net license agreement requires scrolling past 60+ pages of other vendors’ licenses in the narrow box at right.
Another misleading New.net install — disclosed via a one-word on-screen description (“New.net”) without any explanation of function, purpose, or effect. Finding the New.net license agreement requires scrolling past 60+ pages of other vendors’ licenses in the narrow box at right.
New.net finds itself little liked by experts on Internet infrastructure and security. But where are users in this mess? I’ve never spoken with a user who actually wanted New.net, but I’ve looked at plenty of massively-infected computers with New.net installed. So I’ve long suspected nonconsensual, improper, or overly aggressive installations of New.net software.
My suspicions have recently been borne out, because I have repeatedly observed New.net installed via security hole exploits. See this video, made on October 2 in my testing lab. From 0:00 to 0:55, I browse an ordinary web site, 4w-wrestling.com. At 1:07, my computer receives a security exploit — code from Pacimedia syndicated into 4w-wrestling via the Yieldmanager.com ad network. Nine minutes later, Pacimedia installed New.net onto my test machine. See video at 10:30-10:45. See also the top screenshot at right, showing the New.net folder (among others) newly added to my Program Files listing.
Did the Pacimedia installer get user consent to install New.net? Absolutely not. The Pacimedia exploit did show a screen (second image at right), in which it described software “available to be installed.” But nowhere did Pacimedia disclose what programs would be installed; Pacimedia called the software “a free browser enhancement” but gave no names of specific programs or functions. Pacimedia didn’t even link to a separate license, listing, or other document to explain what programs would be installed. Instead, Pacimedia’s installer oddly says users “agree to the terms and conditions stated here” — but neither states nor links to any terms or conditions.
As it turns out, unchecking the mysterious unlabeled checkbox would have prevented the installation of Pacimedia and its bundled programs. But a user cannot be said to have “agreed” to receive New.net (or other software) merely by failing to uncheck a box. And pressing a button labeled “close this window” does not grant consent to install numerous advertising programs.
Of course this isn’t New.net’s only sneaky installation. This spring I looked at eDonkey, which encourages users to install New.net via a pre-checked checkbox, giving New.net’s name and icon, but offering no description of New.net’s effects. Even if a user locates the New.net license — by scrolling through 60+ on-screen pages of other vendors’ licenses — the New.net license still doesn’t explain what New.net does or why a user might (or might not) want it. Such a user cannot reasonably be claimed to have “agreed” to run New.net software.
I’ve also seen New.net in big bundles with other P2P programs, screensavers, and similar. I retain detailed evidence on file. See also Eric Howes’ analysis of New.net as installed by the Good Luck Bear desktop theme — again lacking any explanation of what New.net does.
In its demand letters (e.g. pages 3-4 of its letter to CounterExploitation), New.net has claimed always to “provide[] very detailed download disclosures to all potential users” and to install only with users’ “explicit consent.” These are laudable goals, but they’re not just not achieved by New.net’s actual practices.
So New.net faces a product users don’t want; an Internet community that doesn’t like its core business or their installation tactics; and clear proof of its software installed without user consent. Yet paradoxically some anti-spyware vendors still don’t detect New.net or help users remove New.net software. See Eric Howes’ recent State of New.net Detections — finding that Webroot, Spyware Doctor, and Ad-Aware all fail even to detect New.net, while Microsoft recommends ignoring New.net and Spybot ignores New.net by default.
The Rest of Pacimedia’s Bundle
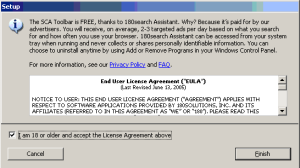 A 180solutions stub installer also shown during the course of the Pacimedia/New.net installation. Paradoxically, 180solutions installs even if users decline the installation in the stub.
A 180solutions stub installer also shown during the course of the Pacimedia/New.net installation. Paradoxically, 180solutions installs even if users decline the installation in the stub.
New.net isn’t all that Pacimedia installs. In my testing, I saw programs installed from ConsumerAlertSystem, ContextPlus, eXact Advertising, Integrated Search Technologies, MediaAccess, Powerscan, SearchAccuracy, ShopAtHomeSelect, Sidefind, SurfSidekick, and YourSiteBar. All are shown in my installation video.
Pacimedia also installed 180 — despite my specific refusal to grant consent when asked. In the video at 7:09, 180 showed a stub installer popup, seeking user consent to install. (See screenshot at right.) I specifically declined 180’s offer. But a mere twelve minutes later, in the video at 19:18, a full copy of 180solutions nonetheless arrived on my test PC. So much for 180’s vaunted new “safe and secure” installation methods: Despite 180’s claims, it’s clear that their software still arrives without consent.
My video also shows the detrimental effects of these many added programs on my test machine: Midway through testing, I couldn’t even load Internet Explorer. Typical users would find it difficult to recover from such a large installation — their computers too badly encumbered even to download an anti-spyware program to begin to clean up the mess.
Though Pacimedia’s installation bundle changes over time, it’s striking how long Pacimedia has continued practices substantially matching what I saw this week. In testing of April 4, 2005, I received the same exploit and same dialog box shown above — even the same false claim that “you agree to the terms and conditions stated here,” with no conditions actually stated. Throughout this period, Pacimedia has received traffic through major ad networks (Yieldmanager.com, as well as Targetnet.com from Mamma Media (Nasdaq: MAMA)), has installed adware from large vendors including 180 and eXact (along with others, often including Direct Revenue), and has simultaneously shown a misleading ActiveX (see separate write-up). It’s hard to defend any of these practices. Yet somehow Pacimedia has continued apace for 6+ months.
For those interested in the technical details of Pacimedia’s security exploit: Pacimedia serves up a page with two IFRAMEs, one of them a reference to a doubly-encoded JavaScript (JScript.Encode followed by Unicode encoding). After decoding, inspection of that page reveals its use of an IE security vulnerability (discovered March 2004), allowing the execution of arbitrary code on a user’s PC. In particular, Pacimedia’s second IFRAME references a CHM, via syntax ms