Current Practices of IAC/Ask Toolbars
- Installation Screenshots
Current Practices of IAC/Ask Toolbars - Ben
Edelman
[ Using the "Ask Jeeves" Name | Advertising on "TheKidzPage" | FullContext Spyware Promoting Ask | SearchingBooth Spyware Promoting Ask | DollarRevenue Spyware Promoting Ask | EULA Link Off-Screen | Resulting PPC Ads | False Statements in Installation Sequence ]
These Toolbars Are Described as Coming from "Ask Jeeves" and "Ask"
Ask's toolbar installations continued to describe Ask's toolbars as coming from "Ask Jeeves, Inc." For example, this designation appears within the code-signing area of the toolbar installer -- the key place where Windows software developers are to label their software with their true and correct name. Screenshot taken on October 13, 2006.

Third-party installers also still prominently claim installations are "by Ask Jeeves." Screenshot taken on October 15, 2006.
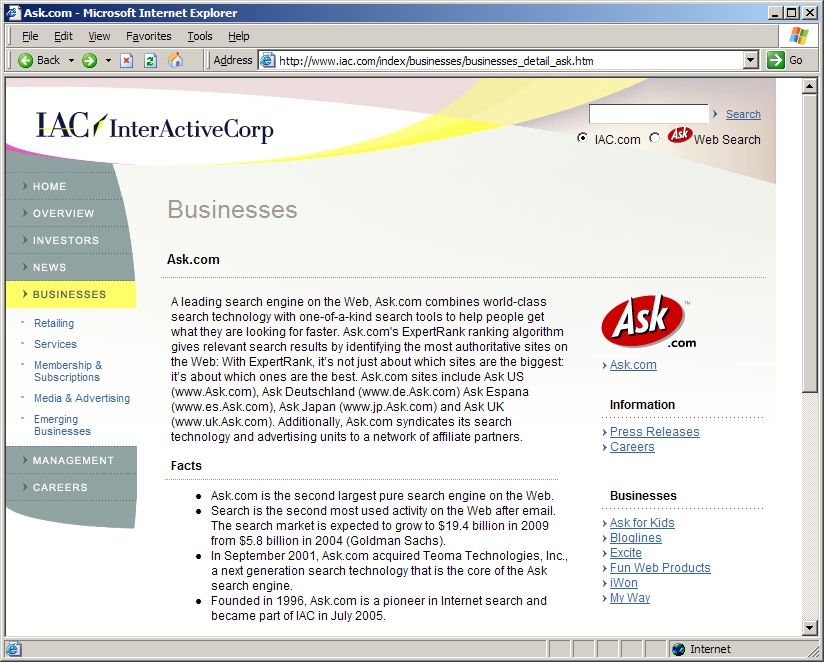
IAC's corporate site describes FunWebProducts (the devision that makes these toolbars) as fallling within Ask.com. Screenshot taken on October 13, 2006:
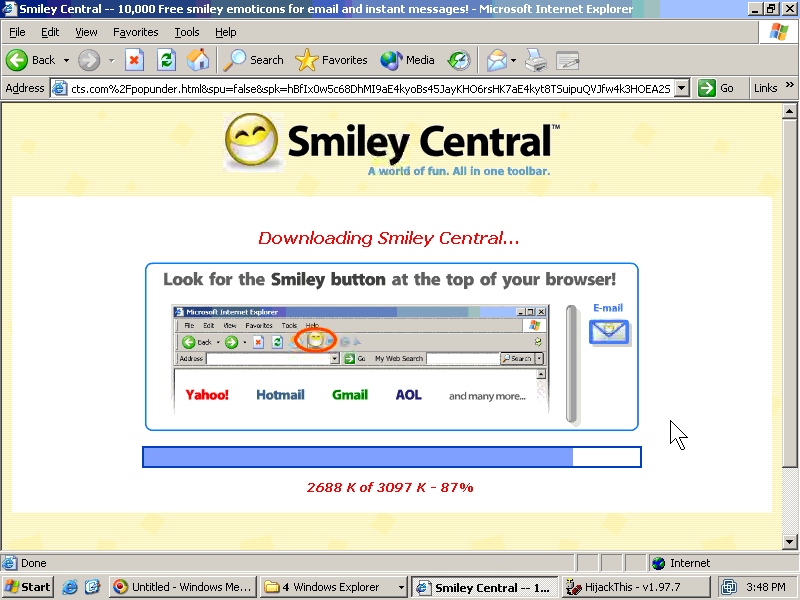
Ask Toolbar Promoted on TheKidzPage
The screenshot below, prepared on September 30, shows an Ask ad (the tall "get fun, new cursors!" ad at screen left) placed on thekidzpage.com, which caters substantially to kids.

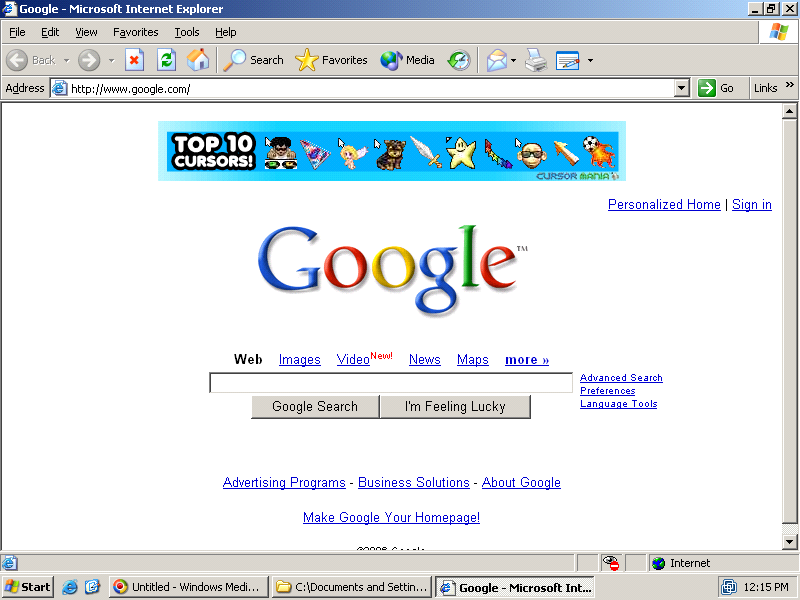
FullContext Injection Promoting Ask
FullContext injects an Ask ad into Google, without Google's permission. Notice the Ask ad at page top-center, a place where Google does not sell ads to any company at any price. FullContext accomplishes this injection using its spyware, which is widely installed onto users' PCs without their consent. Screenshot taken on August 29, 2006.
SearchingBooth shows an Ask "e-Cards" ad as a pop-up. SearchingBooth spyware is widely installed without consent. Screenshot taken on October 2, 2006.

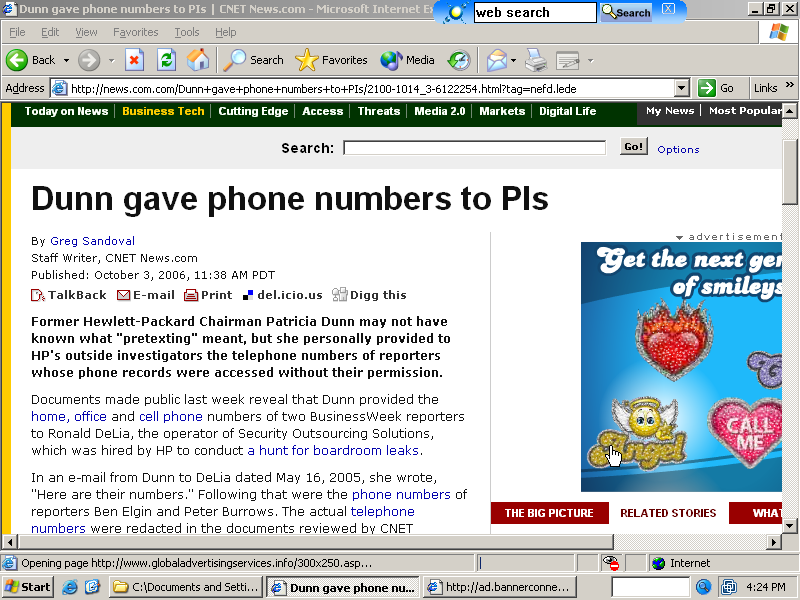
DollarRevenue Promoting Ask, Covering Other Ads
Spyware from DollarRevenue replaced the ad originally shown by c|net News.com, instead showing this Ask "smiley" ad instead. That is, the Ask ad completely and exactly covered the ad c|net had intended to place into this page. I have on file a packet log and video sufficient to prove that this placement was performed by DollarRevenue spyware, not by c|net. Screenshot taken on October 3, 2006.
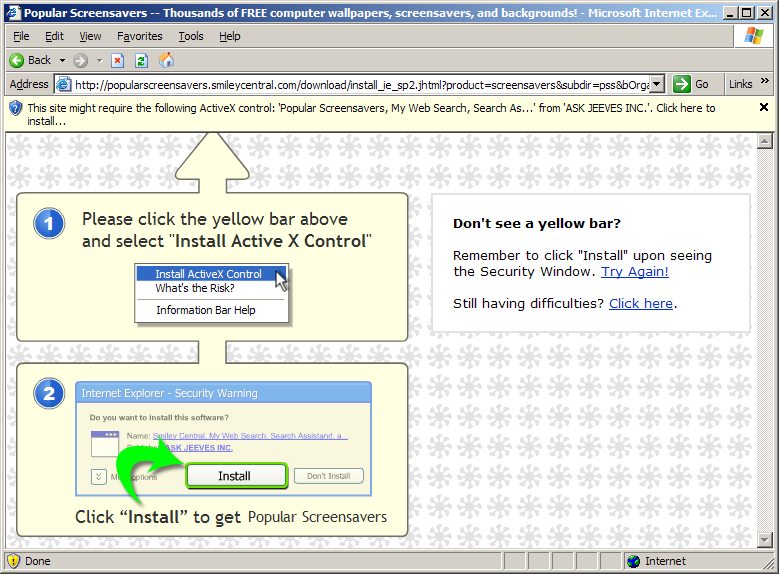
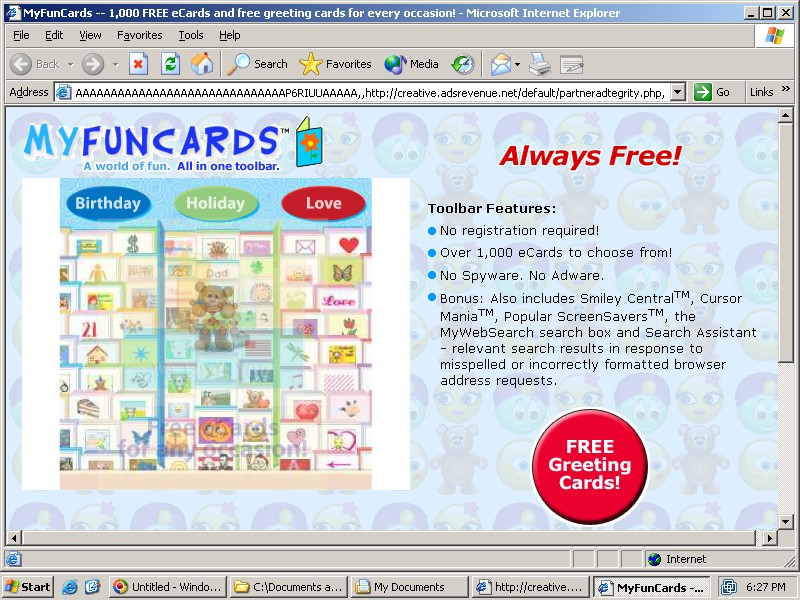
Ad Landing Pages with the EULA Link Off-Screen
Ask staff claim that their landing pages always include a link to Ask's EULA, even when landing pages are viewed on 800x600 screens. That claim is inaccurate. See e.g. the screenshot below, the result of clicking the SearchingBooth-delivered ad shown above. Notice the lack of an on-screen link to the EULA. I retain a video on file showing that this screenshot correctly captures the window exactly as it appeared on my screen. (I did not move, resize, or change the window in any way.) Screenshot taken on October 2, 2006.
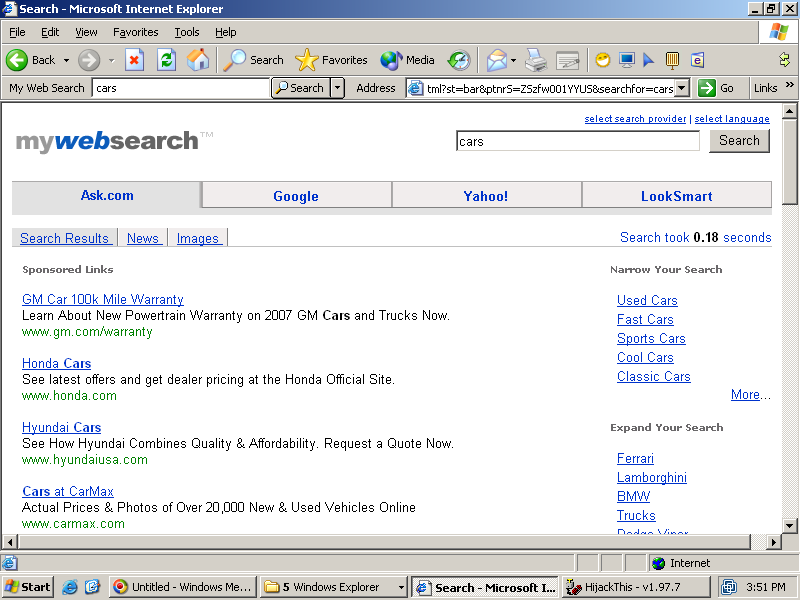
Resulting Landing Pages and Excessive Sponsored Links
Ask's landing pages include unusually numerous and prominent ads. For example, this screenshot shows the first of 2+ pages of sponsored links, all of which appeared above even the first organic (ordinary, non-sponsored) result. Screenshot taken on October 14, 2006.
False Statements in Installation Sequence
This Ask installation statements misrepresent Ask's effects on browser arrangement. In particular, this screen shows Ask's search box ("My Web Search") inserted at the browser's top right, with the Address Bar remaining in its usual position at top-left. In fact Ask's true practice is exactly the opposite. Screenshot made on October 14, 2006.