Are pop-up ads anything more than an annoyance? For advertisers they can certainly be a bad deal — particularly when spyware-delivered pop-ups cheat advertisers through PPC click fraud, PPC syndication fraud, affiliate fraud, banner farms, or other improper ways of getting paid. For users, pop-ups in overwhelming quantities may cause substantial harm — especially because pop-up-delivering spyware reduces computer speed and reliability, and because spyware transmits sensitive user information to remote servers.
But spyware-delivered pop-ups can do more than annoy. They can also offend. Consider spyware that shows sexually-explicit (most would say, pornographic) pop-ups. When such ads appear unrequested, they’re likely to be shown to users who don’t want to see sexually-explicit material. It’s a troubling practice — but all too common even among “adware” vendors that claim to have reformed. Meanwhile, some old tricks remain — like pop-ups with their “X” buttons off-screen, making the ads particularly hard to close.
ZenoTecnico and AlmondNet Showing AdultFriendFinder
 The ZenoTecnico ad, edited to cover sexually-explicit areas.
The ZenoTecnico ad, edited to cover sexually-explicit areas.
money
AlmondNet / ProMarket
money
ZenoTecnico
The money trail for this ad.
Let’s start with a simple example. On a test PC, I browsed the Findromance.com site. That’s definitely a dating site — but it’s not sexually explicit. Many users browse online dating service without wanting to see online porn.
In testing in May 2006, ZenoTecnico served me the pop-up shown at right (modified to cover the bare breasts exposed in the original). ZenoTecnico is notorious spyware which I have seen installed through a variety of misleading bundles and security exploits. Zeno’s web site claims an address in Panama, but I believe this address is a sham. I’m working on identifying their true location.
Packet log analysis shows that traffic flowed in the way shown in the diagram at right: From ZenoTecnico to ProMarket (part of New York-based AlmondNet) to AdultFriendFinder. See also the associated packet log.
Set against the more complex examples that follow, this Zeno-ProMarket-AdultFriendFinder is particularly notable: These three parties alone decided to show this ad, in this way, under these circumstances and with this targeting (or lack thereof), without influence by any other spyware installed on my test PC, and with a reasonably direct relationship between advertiser and spyware vendor, as shown at right. They may blame each other. But as best I can tell, they have no one but each other to blame.
Direct Revenue Showing MorpheusOfPorn
 The Direct Revenue ad, edited to cover explicit areas.
The Direct Revenue ad, edited to cover explicit areas.
money
Direct Revenue
The money trail for this ad.
It’s well-known that most spyware-infected computers contain multiple spyware programs. When multiple spyware programs interact, they are particularly likely to show sexually-explicit images without a user requesting any such materials.
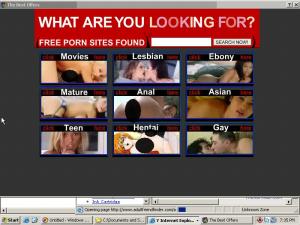
The screenshot at right presents a pop-up shown to me on a massively infected test PC. The pop-up bears Direct Revenue’s branding (“The Best Offers”), and packet log analysis confirms that the ad came through the Direct Revenue pop-up system.
What caused Direct Revenue to show this ad? Mere seconds earlier, unidentified spyware on my test PC had sent traffic to ad network YieldManager, which had in turn redirected me to AdultFriendFinder. Direct Revenue saw that traffic to AdultFriendFinder and took that as a trigger to display the explicit pop-up shown at right. See the associated packet log (showing the preceding YieldManager traffic), as well as a video of the sequence (edited to cover sexually-explicit areas).
Observing my computer’s traffic to AdultFriendFinder.com, Direct Revenue’s advertising software assumed I was seeking sexually-explicit material. But where the AdultFriendFinder site itself appears unrequested, as in my example, Direct Revenue’s assumption is badly in error. To the contrary, sexually-explicit content is unlikely to be desired or appropriate when other spyware has decided to show a user AdultFriendFinder.
Even AdultFriendFinder recognized that it might not be appropriate to show a sexually-explicit image to users reaching its site in the manner captured in my testing. See a screenshot (from video at 2:46) of the landing page AdultFriendFinder showed me. As delivered to my test PC (via the undetermined spyware), AdultFriendFinder’s site included no visible sexually-explicit images. Instead, the page was a mere doorway — with a disclosure (“Warning! You are about to view…”) along with separate links for users above 18 (to enter) and below age 18 (to go elsewhere).
It is particularly notable for Direct Revenue to show unrequested sexually-explicit materials because Direct Revenue has specifically promised not to do so. In the proposed settlement of a consumer class action lawsuit against Direct Revenue, provision (m) specifically requires that Direct Revenue’s software “will not display adult content ads unless the user is viewing adult websites.” In this example, I did not request any adult web site. Neither did I actually view any adult material (prior to the material shown by Direct Revenue): The AdultFriendFinder page at issue cannot be categorized as “adult,” because it includes no sexually-explicit images. In short, on these facts, I see a strong argument that Direct Revenue violated its duties under its settlement agreement.
Deskwizz/SearchingBooth, Z-Quest, YieldManager and Zedo Showing Vitalix
 The SearchingBooth ad, edited to cover explicit areas.
The SearchingBooth ad, edited to cover explicit areas.
money
Zedo
money
YieldManager
money
Z-Quest
money
Deskwizz / SearchingBooth
The money trail for this ad.
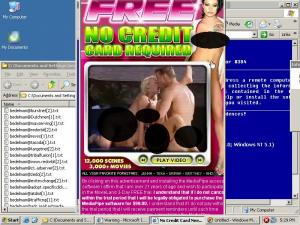
Deskwizz/SearchingBooth shows a variety of intrusive advertisements, largely untargeted. Many of its ads are injected into others’ sites (without those sites’ consent), as in this screenshot showing a Vonage ad injected into the Vistaprint site. The SearchingBooth.com web site gives an address in Quebec. I have repeatedly observed Deskwizz/SearchingBooth installed through exploits and in large bundles (e.g. the Dollarrevenue bundle) without meaningful user consent.
The screenshot at right shows an ad served to me on a PC with SearchingBooth installed. The ad shows a total of four nude individuals, and I have edited the ad to cover sexually-explicit areas.
Packet log analysis indicates that traffic flowed in the following way: First, SearchingBooth spyware sent traffic to its SearchingBooth.com controlling server, seeking an ad to be displayed. SearchingBooth.com replied with a URL to a Z-quest.com (a Canadian company whose site describes meta-search services as well as a toolbar). Z-quest sent me on to YieldManager. YieldManager in turn sent me to Zedo (a San Francisco ad server that features Internet luminary Esther Dyson on its advisory board). Finally, Zedo opened a new window of Vitalix, which showed the sexually-explicit content at issue. These relationships are set out in the diagram at right, in the URL list below, and in the full packet log.
http://banners.searchingbooth.com/advertpro/servlet/view/dynamic/html…
http://ads.z-quest.com/MarkSect720x300.html
http://ad.yieldmanager.com/imp?z=0&s=16185&r=1&y=23&w=720&h=300
http://c5.zedo.com/jsc/c5/ff2.html?n=377;c=40;s=17;d=15;w=1;h=1
http://c4.zedo.com/ads2/d/3869/172/377/40/i4.js?z=5414
http://l5.zedo.com//log/p.html?a=146636;x=3869;g=172,0;c=377000040,37…
http://ads.vitalix.net/ads/3day/wb03/index.html?prov=seedcorn&subprov…
The longer chain of relationships in this example makes it more difficult to determine who is responsible for the unrequested display of sexually-explicit content. One might reasonably blame Deskwizz/SearchingBooth, whose nonconsensually-installed spyware was the root cause of any ad being shown at all. But also responsible is Zedo, which had the last clear chance to prevent the display of this ad, and which showed these sexually-explicit images without obtaining a correct and reliable verification that such a display was appropriate. Meanwhile, ad placement system YieldManager was squarely in the middle of the chain, and YM’s detailed Media Guard blog suggests they’ve thought at length about the special problems of sexually-explicit ads. Yet they too failed to prevent this sexually-explicit ad from appearing unrequested.
Typical users are likely to find this sexually-explicit ad particularly intrusive and particularly hard to remove because the ad’s “X” button appears off-screen. Notice the absence of a title bar, “X” button, or minimize button in the screenshot at right. Sophisticated users may know they can press Alt-F4 to close the ad. But novices don’t. Reviewing the packet log, it appears that Zedo is responsible for this partially-off-screen window placement: The ad is placed in the specified location by JavaScript code served from the Zedo server, which instructs as follows:
zzWindow.moveTo(Math.ceil((screen.availWidth – 380) / 2), Math.ceil((screen.availHeight – 680) / 2));
This code moves the ad window to a vertical location given by the screen’s available height (in pixels) minus 680 (the intended height of the ad at issue), divided by two. If the user’s screen is more than 680 pixels tall, this code has the effect of centering the window vertically on the user’s screen. But if the user’s screen is less than 680 pixels tall, e.g. a 800×600 pixel screen common on many older laptops and some older desktops, then this code predictably and inevitably has the effect of placing the “X” button off-screen. Zedo and its advertiser should have checked the user’s actual screen-height (e.g. via the code “if screen.availHeight>680”), to make sure they were not positioning the pop-up with its “X” off-screen.
Look2me/Ad-w-a-r-e, FirstAdSolution, YieldManager, Falk AG/DoubleClick, eXact Advertising, MyGeek Showing Naughtyplay
 The SearchingBooth ad, edited to cover explicit areas.
The SearchingBooth ad, edited to cover explicit areas.
money
MyGeek
money
Instant Navigation / eXact Advertising
money
Falk AG / DoubleClick
money
YieldManager
money
FirstAdSolution / Oridian
money
Look2me / Ad-w-a-r-e / Intern-etadvertising
The money trail for this ad.
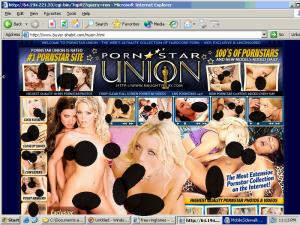
From Minnesota-based NicTech Networks, Look2me/Ad-w-a-r-e spyware is widely installed through security exploits and misleading bundles. Its revenue sources are equally broad. I’ve seen Look2me/Ad-w-a-r-e getting paid by performing click fraud against Yahoo advertisers, and by seizing unearned commission through merchants’ affiliate programs. But Look2me/Ad-w-a-r-e also shows ordinary banner ads and pop-up ads, including untargeted run-of-network ads through sites such as its buyer-shabit.com banner loading page (among many others).
The screenshot at right shows an ad served to me on a PC with Look2me/Ad-w-a-r-e installed. The ad is exceptionally explicit: Its large images show four women completely nude and one partially disrobed, in addition to two protruding male members from men not otherwise pictured. Smaller images show at least sixteen women and ten male members (although not a single male face). In total, the ad pictures at least thirty-three individuals in an overwhelming array of sexual positions. The ad arrived on my screen as a full-screen pop-up, but with its upper-right “X” button entirely off-screen, just as shown in the screenshot and thumbnail.
Packet log analysis indicates that traffic flowed in the following way: First, Look2me sought an ad from its controlling server, Ad-w-a-r-e.com. Ad-w-a-r-e specified an ad at intern-etadvertising.com, a standard Look2me loading page which shows untargeted (run-of-network) ads. Intern-etadvertising specified that the ad was to come from Firstadsolution.com (Oridian Online Media Solutions of Israel), which in turn sent me to YieldManager, which specified that the ad was actually at Falkag.net. Falk AG (recently acquired by DoubleClick) in turn sent me on to Instantnavigation.com (whose Contact Us page indicates that it is part of Brainfox.com, recently acquired by eXact Advertising). Instantnavigation sent me to the 207.97.227.29 server (eXact Advertising), which redirected me to MyGeek, which finally passed me to Naughtyplay, the explicit web site shown in the pop-up.
These relationships are set out in the diagram at right, in the URL list below, and in the full packet log.
http://www.ad-w-a-r-e.com/cgi-bin/UMonitorV2
http://www.intern-etadvertising.com/muon.html
http://ad.firstadsolution.com/imp?z=0&s=3926&u=http%3A%2F%2Fwww.inter…
http://ad.yieldmanager.com/imp?z=0&s=3926&u=http%3A%2F%2Fwww.intern-e…
http://a.as-us.falkag.net/dat/cjf/00/14/73/07.js
http://a.as-us.falkag.net/dat/dlv/aslframe.html?dat=147307&kid=130138…
http://www.instantnavigation.com/search.php?cat=dvd&partner=ap_tk
http://207.97.227.29/clk/?313b313134373035373939352e34327e61705f746b3…
http://xmlsearch.mygeek.com/presults.jsp?partnerid=110126&vendorI…
http://www.naughtyplay.com/pornstars/heatherhunter/index.html
By all indications, the 207.97.227.29 server performed click fraud against MyGeek. The structure and obfuscation of the HTML on that server indicate a special desire to avoid being caught, as does eXact’s unilateral insertion of purported search keywords (“heather hunter”) not specified earlier in the traffic. I have observed nearby server addresses with the same URL syntax serving in a click fraud chain against Yahoo Overture. Furthermore, I understand that the xmlsearch.mygeek.com server runs a pay-per-click advertising system, distinct from MyGeek’s separate “cost per view” system for which advertisers may be charged without a click occurring. Traffic to and through that server, without a bona fide user click, seems to constitute click fraud.
This chain of relationships is notable for its extreme length — five intermediaries between spyware vendor and advertiser. These many relationships provide numerous opportunities for ad context to be lost — for ad networks to fail to tell each other that a sexually-explicit ad is not appropriate here.
Policy Recommendations; The Problem In Context
The four examples shown above are just a tiny portion of the problem of sexually-explicit images shown to users who didn’t request such materials. I have numerous additional examples on file. In one example on file, spyware on my test PC identifies the name of a fashion designer on a well-known retailer’s site, then uses that word as a trigger for an ad, ultimately showing an ad that is sexually-explicit. In another example, spyware on my test PC observes me browsing the children’s section of an online shoe store, a page mentioning “girls” in its title. The spyware then serves me a full-screen sexually-explicit pop-up. Notably, the pop-up was obtained via click fraud against a major pay-per-click search engine.
In my view, unrequested displays of sexually-explicit content largely arise out of the unaccountability pervasive in the spyware space. In each of the examples above, I anticipate that the parties involved will blame each other. Ad networks may claim that other ad networks told them (through tags, attributes, or contracts) that traffic was suitable for sexually-explicit ad display. Spyware vendors will blame other spyware for having suggested that users wanted such content. In all likelihood, no party will take responsibility for the bad outcomes that resulted.
In other contexts, online service providers face serious penalties for showing unrequested sexually-explicit images. Section 521 of the PROTECT Act creates criminal liability (up to two years imprisonment) for “us[ing] a misleading domain name … with the intent to deceive a person into viewing material constituting obscenity”, and additional liability for deceiving minors into viewing material that is harmful to minors. This law responded to the problem of typosquatters and other bulk domain registrants showing adult materials — such that users would stumble onto sexually-explicit images unrequested. But no such law protects users from unrequested pornography shown by spyware.
Even without legislative intervention, well-intentioned ad networks have tools at their disposal to prevent the unrequested display of sexually-explicit materials. One natural approach is to make all ads and landing pages non-explicit. Then a mistaken ad display does not show sexually-explicit materials (although it might still link to such materials). Ad networks could also redouble their supervision of their partners — checking the specific circumstances in which explicit ads may be shown, and confirming that these circumstances leave no doubt that a user actually wanted to receive explicit content. Tough ad networks could create financial incentives that penalize their partners for any errors uncovered — warnings, fines, and contract termination. Finally, ad networks could improve their public statements of applicable policies and procedures, making it easier for consumers to report unwanted images — including helping consumers learn where and how to submit such reports. Ad networks that find these steps too difficult or too costly could simply leave the business of serving or placing sexually-explicit advertisements.
Semi-explicit sites raise particular problems for spyware targeting. In my Direct Revenue example (above) and in various other examples I have on file, AdultFriendFinder buys spyware-delivered traffic and shows ads that, while suggestive, are not sexually-explicit. But then other spyware observes this AdultFriendFinder traffic, using this traffic as a catalyst to show ads that are explicit. Spyware vendors need to recognize that while some AdultFriendFinder ads are explicit (e.g. my first example above), others are not. With AdultFriendFinder’s mix of ads, and with typical spyware-infected PCs running multiple spyware programs, a visit to AdultFriendFinder cannot be interpreted as a proper trigger to show sexually-explicit images. Same for any other sites that buy run-of-network (or other spyware-delivered) advertising, or that otherwise straddle the border between explicit and non-explicit materials.
Yesterday the Direct Marketing Association released best practices for online advertising networks and affiliate marketing.The DMA calls for obtaining assurances of compliance with applicable law, performing due diligence on prospective partners, and monitoring compliance. It’s easy to criticize these approaches as obvious or overdue. But if the ad networks above were using the DMA’s recommended methods, these problems would be substantially less widespread. Meanwhile, I continue to think the DMA’s final recommendation — “develop a system to routinely monitor your ad placements” — remains essential yet under-appreciated. Tough enforcement and real penalties could stop thesepractices: Spyware purveyorswouldn’t run these (or any other) ads if they weren’t getting paid for it.