I’ve written before about unwanted software installed on users’ computers via security holes. For example, in July I mentioned that 180solutions software was being installed through Internet Explorer vulnerabilities. (See also 1, 2, 3) More recently, researchers Andrew Clover and Eric Howes (among others: 1, 2) have described increasing amounts of unwanted software being installed through security holes.
 Malware installed through a single security exploit
Malware installed through a single security exploit
How bad is this problem? How much junk can get installed on a user’s PC by merely visiting a single site? I set out to see for myself — by visiting a single web page taking advantage of a security hole (in an ordinary fresh copy of Windows XP), and by recording what programs that site caused to be installed on my PC. In the course of my testing, my test PC was brought to a virtual stand-still — with at least 16 distinct programs installed. I was not shown licenses or other installation prompts for any of these programs, and I certainly didn’t consent to their installation on my PC.
In my testing, at least the following programs were installed through the security hole exploit: 180solutions, BlazeFind, BookedSpace, CashBack by BargainBuddy, ClickSpring, CoolWebSearch, DyFuca, Hoost, IBIS Toolbar, ISTbar, Power Scan, SideFind, TIB Browser, WebRebates (a TopMoxie distributor), WinAD, and WindUpdates. (All programs are as detected by Ad-Aware.) I have reason to believe that numerous additional programs were also installed but were not detected by Ad-Aware.
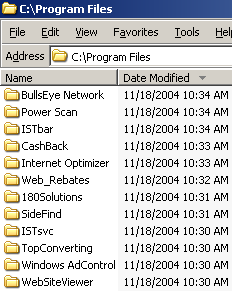
See a video of the installations. The partial screen-shot at left shows some of the new directories created by the security exploit.
Other symptoms of the infection included unwanted toolbars, new desktop icons (including sexually-explicit icons), replacement desktop wallpaper (“warning! you’re in danger! all you do with computer is stored forever in your hard disk … still there and could broke your life!” (s.i.c.)), extra popup ads, nonstandard error pages upon host-not-found and page-not-found error conditions, unrequested additions to my HOSTS file, a new browser home page, and sites added to my browser’s Trusted Sites zone.
I’ve been running similar tests on a daily basis for some time. Not shown in the video and screen-shot above, but installed in some of my other tests: Ebates Moe Money Maker, EliteToolBar, XXXtoolbar, and Your Site Bar.
Installation of 180solutions software through security holes is particularly notable because 180 specifically denies that such installations occur. 180’s “privacy pledge” claims that 180 software is “permission based” and is “programs are only downloaded with user consent and opt-in.” These claims are false as to the installation occuring in the video linked above, and as to other installations I have personally observed. Furthermore, 180’s separate claim of “no hiding” is false when 180 software is installed into nonstandard directories (i.e. into C:Windows rather than a designated folder within Program Files) and when 180 software is installed with a nonstandard name (i.e. sais.exe) rather than a name pertaining to 180’s corporate name or product names.
What’s particularly remarkable about these exploits is that the bad actors here aren’t working for free. Quite the contrary, they’re clearly expecting payment from the makers of the software installed, payments usually calculated on a per-install basis. (For example, see a 2003 message from 180solutions staff offering $0.07 per installation.) By reviewing my network logs, I can see the specific “partner” IDs associated with the installations. If the installers want to get paid, they must have provided accurate payment details (address, bank account number, etc.) to the makers of the programs listed above. So it should be unusually straightforward to track down who’s behind the exploits — just follow the money trail. I’m working on passing on this information to suitable authorities.
Note that the latest version of Internet Explorer, as patched by Windows XP Service Pack 2, is not vulnerable to the installations shown in my video and discussed above.