I’ve long believed that the spyware explosion results primarily from advertisers’ payments. It’s easy to see why advertisers love spyware: Where better to get a customer, than someone who is about to buy from a direct competitor? And spyware-delivered ads are so exceptionally intrusive — often full-screen pop-ups — that they’re likely to drive sales, even if users dislike the pop-up format.
Spyware advertising also suffers from a race-to-the-bottom effect. Consider a two-party example. If Expedia serves a big pop-up when users visit Orbitz, Expedia is likely to get lots of new customers from Orbitz. What should Orbitz do in response? They could sue, as many companies have. But more likely, they’ll just buy more spyware-delivered ads of their own — and try to grab back some of the users Expedia just took away. This yields high revenue to spyware vendors (in turn yielding more spyware), high costs to advertisers, and annoying popups for users. It’s nothing to celebrate.
With this problem in mind, I’ve written at length about spyware revenue models. My publications page shows a dozen articles on this subject, dating back to my 2003 report of advertisers using Gator (now Claria).
 Today, the Center for Democracy and Technology posted a report (PDF) on the spyware advertising problem. Earlier this year, I provided CDT with a number of examples of advertisers still funding 180solutions (despite 180’s many known nonconsensual installations and other bad practices). See also my thumbnails of the ads I saw.
Today, the Center for Democracy and Technology posted a report (PDF) on the spyware advertising problem. Earlier this year, I provided CDT with a number of examples of advertisers still funding 180solutions (despite 180’s many known nonconsensual installations and other bad practices). See also my thumbnails of the ads I saw.
CDT’s report rightly criticizes advertisers that lack a policy for where their ads can appear. Of course just having a policy may not be enough. Apparently the travel industry has developed such a policy — yet I still see big travel companies advertising with Claria, Hotbar, and others. And travel companies’ partners and affiliates continue to advertise through the most notorious of spyware.
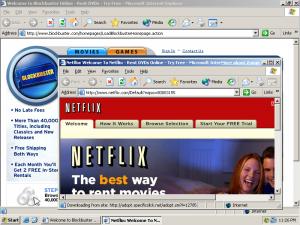
What comes next here? I’ve been pleased to see responsible advertisers withdrawing from the big-name spyware vendors — with a corresponding reduction on the number of users those vendors harm. That said, when advertisers terminate their direct relationships with spyware vendors, spyware vendors often find indirect ways to continue to get paid by the same advertisers. For example, spyware vendors show lots of pay-per-click ads (as I documented last year for Yahoo and Google [1, 2]). Spyware vendors also show affiliate ads (index of findings, some specific examples), syndicated banners, and more. At last week’s NYU/Princeton spyware conference, I showed new examples of some of these indirect relationships — including an example that combines spyware with click fraud against a Yahoo advertiser (slides 17-19). And CDT’s report (PDF, page 9) mentions my finding of many Netflix ads appearing through these indirect relationships, even after Netflix claimed my first example was “unique.” Common to all these examples: Advertisers’ ads appear in ways they didn’t specifically intend and often don’t even know about; and spyware vendors ultimately benefit from advertisers’ inattentiveness.
These ad syndication relationships will be a renewed priority for discussion on my site in the coming months. Sophisticated advertisers and ad networks need to understand that merely writing an ad policy won’t stop these bad relationships. Instead, advertisers need to establish testing procedures to make sure their ads actually comply with intended policy.