Video and advertising conglomerate Blinkx tells investors its “strong performance” results from “strategic initiatives” and “expanding demand, content, and audiences.” Indeed, Blinkx recently climbed past a $1.2 billion valuation. At first glance, it sounds like a great business. But looking more carefully, I see reason for grave doubts.
My concerns result in large part from the longstanding practices of two of Blinkx’s key acquisitions, Zango and AdOn. But concerns extend even to Blinkx’s namesake video site. In the following sections, I address each in turn. Specifically, I show ex-Zango adware still sneaking onto users’ computers and still defrauding advertisers. I show the ex-AdOn traffic broker still sending invisible, popup, and other tainted traffic. I show Blinkx’ namesake site, Blinkx.com, leading users through a maze of low-content pages, while charging advertisers for video ads systematically not visible to users.
The Legacy Zango (Adware) Business
In April 2009, Blinkx acquired a portion of Zango, a notorious adware vendor known for products that at various times included 180 Search Assistant, ePipo, Hotbar, Media Gateway, MossySky, n-Case, Pinball, Seekmo, SpamBlockerUtility, and more. Zango was best known for its deceptive and even nonconsensual installations — in write-ups from 2004 to 2008, I showed Zango installing through security exploits (even after design updates purportedly preventing such installations by supposed rogue partners), targeting kids and using misleading statements, euphemisms, and material omissions, installing via deceptive ActiveX popups, These and other practices attracted FTC attention, and in a November 2006 settlement, Zango promised to cease deceptive installations as well as provide corrective disclosures and pay a $3 million penalty.
Few users would affirmatively request adware that shows extra pop-ups, so Blinkx and its distributors use deceptive tactics to sneak adware onto users’ computers. In a representative example, I ran a Google search for “Chrome” (Google’s well-known web browser), clicked an ad, and ended up at Youdownloaders.com — a site that bundles Chrome with third-party advertising software. (The Youdownloaders footer states “The installers are compliant with the original software manufacturer’s policies and terms & conditions” though it seems this claim is untrue: Chrome Terms of Service section 5.3 disallows copying and redistributing Chrome; 8.6 disallows use of Google’s trademarks in a way that is likely to cause confusion; 9.3 disallows transfer of rights in Chrome.) In my testing, the Youdownloaders installer presented offers for five different adware programs and other third-party applications, among them Weather Alerts from desktopweatheralerts.com. Installation video.
I consider the Youdownloaders installation deceptive for at least four reasons: 1) A user’s request for free Chrome software is not a proper circumstance to tout adware. The user gets absolutely nothing in exchange for supposed “agreement” to receive the adware; Chrome is easily and widely available for free, without adware. It is particularly one-sided to install five separate adware apps — taking advantage of users who do not understand what they are asked to accept (including kids, non-native speakers, and those in a hurry). 2) On the Weather Alerts page of the installation, on-screen statements mention nothing of pop-up ads or, indeed, any advertising at all. In contrast, the FTC’s settlement with Zango requires that disclosure of advertising practices be “clear and prominent,” “unavoidable,” and separate from any license agreement — requirements not satisfied here. 3) The Youdownloaders user interface leads users to think that the bundled installations are compulsory. For example, the “decline” button (which lets a user reject each adware app) appears without the distinctive shape, outline, color, or font of an ordinary Windows button. 4) Users are asked to accept an objectively unreasonable volume of agreements and contracts, which in my testing include at least 14 different documents totaling 37,564 words (8.5 times the length of the US Constitution).
Tellingly, Blinkx takes considerable steps to distance itself from these deceptive practices. For example, nothing on Blinkx’s site indicates that Weather Alerts is a Blinkx app or shows Blinkx ads. The Desktopweatheralerts.com site offers no name or address, even on its Contact Us form. Weather Alerts comes from a company called Local Weather LLC, an alter ego of Weather Notifications LLC, both of Minneapolis MN, with no stated affiliation with Blinkx. Weather Notifications’ listed address is a one-bedroom one-bathroom apartment — hardly a standard corporate office. Nonetheless, multiple factors indicate to me that Desktop Weather Alerts is delivers a version of Zango adware. For one, Desktop Weather Alerts popups use the distinctive format long associated with Zango, including the distinctive browser buttons at top-left, as well as distinctive format of the advertisement label at bottom-left. Similarly, many sections of the license agreement and privacy policy are copied verbatim from longstanding Zango terms. Within the Weather Alerts EXE, strings reference 180search Assistant (a prior Zango product name) as well as 180client and various control systems long associated with Zango’s ad-targeting system. Similarly, when Weather Alerts delivers ads, its ad-delivery communications use a distinctive proprietary HTTP syntax both for request (to showme.aspx, with a HTTP POST parameter of epostdata= providing encoded ad context) and response (a series of HTML FORM elements, most importantly an INPUT NAME=ad_url to indicate the popup to open). I have seen this syntax (and its predecessors) in Zango apps for roughly a decade, but I have never seen this syntax used by any advertising delivered by other adware vendors or other companies. Moreover, when a Blinkx contractor previously contacted a security vendor to request whitelist treatment of its adware, the Blinkx representative said “The client is Blinkx … Your engine … was flagging their installer package SWA as SevereWeatherAlerts…” (emphasis added). Notice the Blinkx representative indicating that SWA (another Local Weather program, virtually identical save for domain name and product name) is “their” app, necessarily referring to Blinkx. Finally, in a February 2014 presentation, Blinkx CEO Brian Mukherjee included the distinctive Local Weather icon (present throughout the LW app and in LW’s installation solicitations) as part of the “Blinkx Ecosystem” — further confirming the link between LW and Blinkx. Taken together, these factors give good reason to conclude that Local Weather is applications are powered by Blinkx and part of the Blinkx network. Furthermore, in my testing Blinkx is the sole source of advertising for Weather Alerts — meaning that Blinkx’s payments are Weather Alerts’ primary source of revenue and primary reason for existence. (Additions made February 13, 2014, shown in grey highlighting.)
Meanwhile, Zango-delivered advertising remains a major cause of concern. Zango’s core advertising product remains the browser popup — a disruptive form of advertising unpopular with most users and also unpopular with most mainstream advertisers. Notably, Zango’s popups perpetrate various advertising fraud, most notably ‘lead stealing” affiliate windows that cover merchant sites with their own affiliate links. If the user purchases through either window, the Zango advertiser gets paid a commission — despite doing nothing to genuinely cause or encourage the user’s purchase. (Indeed, the popup interrupts the user and thereby somewhat discourages a purchase.) At right, I show a current example: In testing of January 19, 2014, Blinkx/Zango sees a user browsing Walmart, then opens a popup to Blinkx/LeadImpact (server lipixeltrack) which redirects to LinkShare affiliate ORsWWZomRM8 and on to Walmart. Packet log proof. Thus, Walmart ends up having to pay an affiliate commission on traffic it already had — a breach of Walmart’s affiliate rules and broadly the same as the practice for which two eBay affiliates last year pled guilty. I’ve reported Zango software used for this same scheme since June 2004. As shown at right and in other recent examples, Zango remains distinctively useful to rogue affiliates perpetrating these schemes. These rogue affiliates pay Blinkx to show the popups that set the scheme in motion — and I see no sign that Blinkx has done anything to block this practice.
Rather than put a stop to these practices, Blinkx largely attempts to distance itself from Zango’s legacy business. For one, Blinkx is less than forthright as to what exactly it purchased. In Blinkx’s 2010 financial report, the first formal investor statement to discuss the acquisition, Blinkx never uses the word “Zango” or otherwise indicates the specific company or assets that Blinkx acquired. Rather, Blinkx describes the purchase as “certain net assets from a consortium of financial institutions to facilitate the growth of the video search and advertising businesses.” If a reader didn’t already know what Blinkx had bought, this vague statement would do nothing to assist.
Even when Blinkx discusses the Zango acquisition, it is less than forthcoming. UK news publication The Register quotes an unnamed Blinkx spokeswoman saying that Blinkx “purchased some technical assets from the bank [that foreclosed on Zango] including some IP and hardware, which constituted about 10 per cent of Zango’s total assets.” Here too, readers are left to wonder what assets are actually at issue. A natural interpretation of the quote is that Blinkx purchased trademarks, domain names, or patents plus general-purpose servers — all consistent with shutting the controversial Zango business. But in fact my testing reveals the opposite: Blinkx continues to run key aspects of Zango’s business: legacy Zango installations continue to function as usual and continue to show ads, and Blinkx continues to solicit new installations via the same methods, programs, and partners that Zango previously used. Furthermore, key Zango staff joined Blinkx, facilitating the continuation of the Zango business. Consider Val Sanford, previously a Vice President at Zango; her LinkedIn profile confirms that she stayed with Blinkx for three years after the acquisition. I struggle to reconcile these observations with the claim that Blinkx only purchased 10% of Zango or that the purchase was limited to “IP and hardware.” Furthermore, ex-Zango CTO Ken Smith contemporaneously disputed the 10% claim, insisting that “Blinkx acquired fully 100% of Zango’s assets.”
Blinkx has been equally circumspect as to the size of the ex-Zango business. In Blinkx’ 2010 financial report, Blinkx nowhere tells investors the revenue or profit resulting from Zango’s business. Rather, Blinkx insists “It is not practical to determine the financial effect of the purchased net assets…. The Group’s core products and those purchased have been integrated and the operations merged such that it is not practical to determine the portion of the result that specifically relates to these assets.” I find this statement puzzling. The ex-Zango business is logically freestanding — for example, separate relationships with the partners who install the adware on users’ computers. I see no proper reason why the results of the ex-Zango business could not be reported separately. Investors might reasonably want to know how much of Blinkx’s business comes from the controversial ex-Zango activities.
Indeed, Blinkx’s investor statements make no mention whatsoever of Zango, adware, pop-ups, or browser plug-ins of any kind in any annual reports, presentations, or other public disclosures. (I downloaded all such documents from Blinkx’ Financial Results page and ran full-text search, finding no matches.) As best I can tell, Blinkx also failed to mention these endeavors in conference calls or other official public communications. In a December 2013 conference call, Jefferies analyst David Reynolds asked Blinkx about its top sources of traffic/supply, and management refused to answer — in sharp contrast to other firms that disclose their largest and most significant relationships.
In March-April 2012, many ex-Zango staff left Blinkx en masse. Many ended up at Verti Technology Group, a company specializing in adware distribution. Myriad factors indicate that Blinkx controls Verti: 1) According to LinkedIn, Verti has eight current employees of which five are former employees of Zango, Pinball, and/or Blinkx. Other recent Verti employees include Val Sanford, who moved from Zango to Blinkx to Verti. 2) Blinkx’s Twitter account: Blinkx follows just nineteen users including Blinkx’s founder, various of its acquisitions (including Prime Visibility / AdOn and Rhythm New Media), and several of their staff. Blinkx follows Verti’s primary account as well as the personal account of a Verti manager. 3) Washington Secretaty of State filings indicate that Verti’s president is Colm Doyle (then Directory of Technology at Blinkx, though he subsequently returned to HP Autonomy) and secretary, treasurer, and chairman is Erin Laye (Director of Project Management at Blinkx). Doyle and Laye’s links to Blinkx were suppressed somewhat in that both, at formation, specified their home addresses instead of their Blinkx office. 4) Whois links several Verti domains to Blinkx nameservers. (Details on file.) Taken together, these facts suggest that Blinkx attempted to move a controversial business line to a subsidiary which the public is less likely to recognize as part of Blinkx.
In November 2011, Blinkx acquired Prime Visibility Media Group, best known for the business previously known as AdOn Network and MyGeek. I have critiqued AdOn’s traffic repeatedly: AdOn first caught my eye when it boasted of relationships with 180solutions/Zango and Direct Revenue. New York Attorney General litigation documents later revealed that AdOn distributed more than 130,000 copies of notorious Direct Revenue spyware. I later repeatedly reported AdOn facilitating affiliate fraud, inflating sites’ traffic stats, showing unrequested sexually-explicit images, and intermediating traffic that led to Google click fraud.
Similar problems continue. For example, in a February 2013 report for a client, I found a botnet sending click fraud traffic through AdOn’s ad-feeds.com server en route to advertisers. In an August 2013 report for a different client, I found invisible IFRAMEs sending traffic to AdOn’s bing-usa.com and xmladfeed.com servers, again en route to advertisers. Note also the deceptive use of Microsoft’s Bing trademark — falsely suggesting that this tainted traffic is in some way authorized by or affiliated with Bing, when in fact the traffic comes from AdOn’s partners. Moreover, the traffic was entirely random and untargeted — keywords suggested literally at random, entirely unrelated to any aspect of user interests. In other instances, I found AdOn receiving traffic directly from Zango adware. All told, I reported 20+ distinct sequences of tainted AdOn traffic to clients during 2013. AdOn’s low-quality traffic is ongoing: Advertisers buying from AdOn receive invisible traffic, adware/malware-originating traffic, and other tainted traffic that sophisticated advertisers do not want.
Industry sources confirm my concern. For example, a June 2013 Ad Week article quotes one publisher calling AdOn “just about the worst” at providing low-quality traffic, while another flags “crazy traffic patterns.” In subsequent finger-pointing as to tainted traffic to OneScreen sites, OneScreen blamed a partner, Touchstorm, for working with AdOn — wasting no words to explain why buying from AdOn is undesirable. Even intentional AdOn customers report disappointing quality: In comments on a posting by Gauher Chaudhry, AdOn advertisers call AdOn “the reason I stopped doing any PPV [pay-per-view] … this is bot traffic”, “junk”, and “really smell[s] like fake traffic.” Of 31 comments in this thread, not one praised AdOn traffic quality.
Recent statements from AdOn employees confirm undesirable characteristics of AdOn traffic. Matthew Papke’s LinkedIn page lists him as Director of Contextual Ads at AdOn. But his page previously described AdOn’s offering as “pop traffic” — admitting undesirable non-user-requested pop-up inventory. His page called the traffic “install based” — indicating that the traffic comes not from genuine web pages, but from adware installed on users’ computers. See screenshot at right. All of these statements have been removed from the current version of Matthew’s page.
Problems at Blinkx.com: Low-Quality Traffic, Low-Quality Content, and Invisible Ads
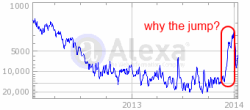 Alexa reports a sharp jump in Blinkx traffic in late 2013.
Alexa reports a sharp jump in Blinkx traffic in late 2013.
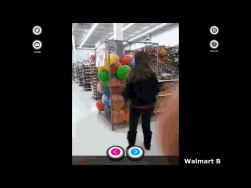 Zango adware caused my computer to display this page from the Blinkx site, full-screen and without standard window controls.
Zango adware caused my computer to display this page from the Blinkx site, full-screen and without standard window controls.
Blinkx’s namesake service is the video site Blinkx.com. Historically, this site has been a bit of an also-ran — it’s certainly no YouTube! But Alexa reports a striking jump in Blinkx popularity as of late 2013: Blinkx’s traffic jumped from rank of roughly 15,000 worldwide to, at peak, rank of approximately 3,000. What could explain such a sudden jump?
In my automated and manual testing of Zango adware, I’ve recently begun to see Zango forcing users to visit the Blinkx site. The screenshot at right gives an example. My test computer displayed Blinkx full-screen, without title bar, address bar, or standard window buttons to close or minimize. See also a partial packet log, wherein the Blinkx site attributes this traffic to Mossysky (“domain=mossysky”), one of the Zango brand names. It’s a strikingly intrusive display — no wonder users are complaining, about their computers being unusable due to Blinkx’s unwanted intrusion. See e.g. a December 2013 Mozilla forum post reporting “my computer has been taken over by malware, half the links are inaccessible because of hovering links to Blinkx,” and a critique and screenshot showing an example of these hovering links. On a Microsoft support forum, one user reports Internet Explorer automatically “opening … numerous BLINKX websites” — as many as “20 websites open at one time, all Blinkx related.”
Moreover, Alexa’s analysis of Blinkx visitor origins confirms the anomalies in this traffic. Of the top ten sites sending traffic to Blinkx, according to Alexa, six are Blinkx servers, largely used to forward and redirect traffic (networksad.com, advertisermarkets.com, networksads.com, advertiserdigital.com, blinkxcore.com, and networksmarkets.com). See Alexa’s Site Info for Blinkx.com at heading “Where do Blinkx.com’s visitors come from?”
Strikingly, Zango began sending traffic to Blinkx during the winter 2013 holiday season — a time of year when ad prices are unusually high. Zango’s popups of Blinkx seem to have ended as suddenly as they began — consistent with Blinkx wanting extra traffic and ad revenue when ad prices are high, but concluding that continuing this practice at length risks excessive scrutiny from both consumers and advertisers.
Meanwhile, examining Blinkx.com, I’m struck by the lack of useful content. I used the Google search site:blinkx.com to find the parts of the Blinkx site that, according to Google, are most popular. I was directed to tv.blinkx.com, where the page title says users can “Watch full episodes of TV shows online.” I clicked “60 Minutes” and received a page correctly profiling the excellence of that show (“the granddaddy of news magazines”). But when I clicked to watch one of the listed episodes, I found nothing of the kind: Requesting “The Death and Life of Asheboro, Stealing History, The Face of the Franchise,” I was told to “click here to watch on cbs.com” — but the link actually took me to a 1:33 minute home video of a dog lying on the floor, “Husky Says No to Kennel”, syndicated from YouTube, entirely unrelated to the top-quality 60 Minutes content I had requested. (Screen-capture video.) It was a poor experience — not the kind of content likely to cause users to favor Blinkx’s service. I tried several other shows supposedly available — The Colbert Report, The Daily Show with Jon Stewart, Family Guy, and more — and never received any of the listed content.
In parallel, the Blinkx site simultaneously perpetrated a remarkable scheme against advertisers: On the video index page for each TV show, video advertising was triggered to play as I exited each page by clicking to view the supposed video content. Because the supposed content opened in a new tab, the prior tab remained active and could still host a video player with advertising. Of course the prior tab was necessarily out of visibility: Blinkx’s code had just commanded the opening of a new tab showing the new destination. But the video still played, and video advertisers were still billed. Screen-capture video.
Industry sources confirm concerns about Blinkx ad visibility. For example, a December 15, 2013 Ad Week piece reported Vindico analysis finding just 23% of Blinkx videos viewable (defined as just 50% of pixels visible for just one second). By Vindico’s analysis, an advertiser buying video ads from Blinkx suffers three ads entirely invisible for every ad visible even by that low standard — a remarkably poor rate of visibility. In contrast, mainstream video sites like CBS and MSN enjoyed viewability rates two to four times higher.
| Q3 ’13 Headcount | ’13 Revenue ($mm) | revenue / headcount ($k) | |
| Tremor | 287 | $148 | $517 |
| YuMe | 357* | $157 | $440 |
| RocketFuel | 552 | $240 | $434 |
| Criteo | 452 | $240 | $532 |
| Blinkx | 265** | $246*** | $927 |
* Q3 ’13 headcount not available. 357 is 2012 year-end. S&M spend up ~50% in 2013. Adjusted revenue/headcount is $293k
** Q3 ’13 headcount not available. 265 is 2012 year-end. S&M spend up ~15% in 2013. Adjusted revenue/headcount is $803k.
*** 2013 revenue estimate based on Bloomberg consensus estimates
Comparing Blinkx’s revenues to competitors, I am struck by Blinkx’s apparent outsized success. See the table at right, finding Blinkx producing roughly twice as much revenue per employee as online video/display ad networks and advertising technology companies which have recently made public offerings. Looking at Blinkx’s sites and services, one doesn’t get the sense that Blinkx’s service is twice as good, or its employees twice as productive, as the other companies listed. So why does Blinkx earn twice as much revenue per employee? One natural hypothesis is that Blinkx is in a significantly different business. While other services make significant payments to publishers for use of their video content, my browsing of Blinkx.com revealed no distinctive content obviously licensed from high-quality high-cost publishers. I would not be surprised to see outsized short-term profits in adware, forced-visit traffic, and other black-hat practices of the sort used by some of the companies Blinkx has acquired. But neither are these practices likely to be sustainable in the long run.
Reviewing Blinkx’s statements to investors, I was struck by the opacity. How exactly does Blinkx make money? How much comes from the legacy Zango and AdOn businesses that consumers and advertisers pointedly disfavor? Why are so many of Blinkx’s metrics out of line with competitors? The investor statements raise many questions but offer few answers. I submit that Blinkx is carefully withholding this information because the company has much to hide. If I traded in the companies I write about (I don’t!), I’d be short Blinkx.
This article draws in part on research I prepared for a client that sought to know more about Blinkx’s historic and current practices. At my request, the client agreed to let me include portions of that research in this publicly-available posting. My work for that client yielded a portion of the research presented in this article, though I also conducted significant additional research and drew on prior work dating back to 2004. My agreement with the client did not oblige me to circulate my findings as an article or in any other way; to my knowledge, the client’s primary interest was in learning more about Blinkx ‘s business, not in assuring that I tell others. By agreement with the client, I am not permitted to reveal its name, but I can indicate that the client is two US investment firms and that I performed the research during December 2013 to January 2014. The client tells me that it did not change its position on Blinkx after reading my article. (Disclosure updated and expanded on February 4-5, 2014.)
I thank Eric Howes, Principal Lab Researcher at ThreatTrack Security, and Matthew Mesa, Threat Researcher at ThreatTrack Security, for insight on current Blinkx installations.