I’ve long been a fan of online shopping site Ebates. Sign up for their service, visit their web site, click through their special links to merchants (including merchants as distinguished as Dell, Expedia, IBM, and L.L. Bean), and earn a small cash back, generally a few percent of your purchase.
But another side of Ebates’ business has become controversial: Ebates uses a software download called “Moe Money Maker” (MMM) to automatically claim merchants’ affiliate commissions, then pay users rebates — even if users don’t visit Ebates’ web site, and even if users don’t click through Ebates’ special links.
Why the controversy? I see at least two worries:
1) Aggressive software installations.
-
 Partial screen-shot taken from video of Ebates installation through a security hole, without any notice or consent.
Partial screen-shot taken from video of Ebates installation through a security hole, without any notice or consent.Users visiting ebates.com can receive MMM software merely by filling out a form and failing to uncheck the “I would like to download MMM” checkbox (checked by default).
- Users downloading certain third-party programs (screen-savers and the like) receive MMM as part of the bundle — disclosed, in my testing, but often with a long license in a small box, such that many users don’t fully understand what they’re getting.
- Most troublingly, there have been persistent allegations of Ebates installed without any notice or consent whatsoever. I had always discounted these allegations until I saw the proof for myself earlier last month. See video of Ebates MMM installed through security holes.
2) Claiming affiliate commissions that would otherwise accrue to other affiliates. Many web sites receive affiliate commissions when users make purchases through special links to merchants’ web sites. (See e.g. Lawrence Lessig‘s “Get It Here” page.) Network rules (Commission Junction , Linkshare) prohibit Ebates from interceding in these transactions; instead, the independent web sites are to receive the commissions for purchases through their links. But Ebates’ software sometimes claims commissions anyway — specifically contrary to applicable rules. These behaviors have been alleged and reported for years, and recently documented in a series of videos (videos of particular interest. Apple, Cooking.com, Diamonds International, JJill, Lillian Vernon, Sharper Image, Sony). If Ebates’ prohibited interventions were only temporary, they would be easy to sweep away as mere malfunctions. But when problems continue for years, to Ebates’ direct financial benefit and to others’ detriment, the behavior becomes harder to disregard.
Meanwhile, Ebates has inspired copy-cat programs with similar business models but even more controversial execution. I’ve recently made literally scores of videos of eXactAdvertising‘s CashBack by BargainBuddy installed through security holes, and also of TopRebates/WebRebates installed through security holes — always without any notice or consent whatsoever. These programs remain participants in the Commission Junction and LinkShare networks — presumably receiving commissions from these networks and their many merchants (CashBack merchants, TopRebates merchants). I’m surprised that so many merchants continue to do business with these software providers — including so many big merchants, who in other contexts would never consider partnering with software installed without notice and consent.
I think the core problem here is skewed incentives. Affiliate networks (CJ and LinkShare) have no financial incentive to limit Ebates’ operation. Instead, the more commissions claimed by Ebates, the more money flows through the networks — letting the networks charge fees of their own. In principle we might expect merchants to refuse to pay commissions not fairly earned — but merchants’ affiliate managers sometimes have secondary motives too. In particular, affiliate managers tend to get bonuses when their affiliate programs grow, which surely makes them particularly hesitant to turn away the large transaction volume brought by MMM’s automatic commission system. That’s not to say some merchants don’t knowingly and intentionally participate in Ebates — some merchants understand that they’ll be paying Ebates a commission on users’ purchases even when users type in merchants’ web addresses directly, and some merchants don’t mind paying these fees. But on the whole I worry that Ebates isn’t doing much good for many merchants, even as its software comes to be installed on more and users’ PCs, with or without their consent.
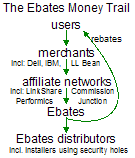 For users who share my continued interest in following the money trail, the diagram at right summarizes Ebates’ complicated business model. Users make purchases from merchants, causing merchants to pay affiliate commissions (via affiliate networks such as LinkShare and Commission Junction) to Ebates. Ebates in turn pays commissions to those who cause its software to be installed, including those installers who install Ebates’ software through security holes, without notice or consent.
For users who share my continued interest in following the money trail, the diagram at right summarizes Ebates’ complicated business model. Users make purchases from merchants, causing merchants to pay affiliate commissions (via affiliate networks such as LinkShare and Commission Junction) to Ebates. Ebates in turn pays commissions to those who cause its software to be installed, including those installers who install Ebates’ software through security holes, without notice or consent.
Ebates Terms & Conditions Allow Removing Other Programs
Finally, note that Ebates has joined the ranks of software providers who, in their EULAs, claim the right to remove other software programs. Ebates’ MMM Terms & Conditions demand:
“Ebates may disable or uninstall any other product or software tool that might interfere with the operability of the Moe Money Maker Software or otherwise preempt or render inoperative the Moe Money Maker Software … In installing the Moe Money Maker Software, you authorize Ebates to disable, uninstall, or delete any application or software that might, in Ebates’ opinion nullify its function.”
Ebates is right to worry that a user can only successfully run a single automatic commission-claiming program. But this license language allows Ebates to delete far more than competing commission programs. For example, if Ad-Aware removes MMM as spyware, thereby “interfering with the operability” of MMM, then the license purports to give Ebates the right to remove Ad-Aware.
Update (December 15): Ebates staff wrote to me to report that they have narrowed the clause quoted above. Ebates’ current Terms allow disabling only “shoping or discount software,” not general-purpose software removal tools like Ad-Aware. Ebates staff further note that they have never exercised the rights granted under the prior Terms text. However, Archive.org reports that Ebates’ Terms included the broad “any application or software” language as long ago as August 2003.
Thanks to Ian Lee, Internet Marketing Strategist & Affiliate Manager of ADS-Links.com, for recommendations on video production methods.
Direct Revenue Deletes Competitors from Users’ Disks updated February 8, 2005
For companies making programs that show users extra pop-up ads, one persistent problem is that users are bound to take action once their computers get too clogged with unwanted software. Find a removal tool, hire a technician, reinstall Windows, buy a new computer, or just stop using the Internet — whatever users do, the pop-up companies won’t make any more money if users don’t keep surfing, and don’t keep clicking the ads. The problem is all the worse because so many unwanted programs install others (usually in exchange for a per-install commission). So if a user has one program showing extra pop-ups, the user might soon have five more.
What’s an “adware” company to do? Direct Revenue has one idea: Delete its competitors’ programs from users’ hard disks. With the other programs gone, users’ computers will run more or less as usual — showing some extra ads from Direct Revenue, but perhaps not attracting so much attention that users take steps to remove all unwanted software.
Direct Revenue’s End User License Agreement provides, in relevant part:
“[Y]ou further understand and agree, by installing the Software, that BetterInternet and/or the Software may, without any further prior notice to you, remove, disable or render inoperative other adware programs resident on your computer …”
In my recent testing, I’ve observed the removals Direct Revenue’s EULA seems to anticipate. And I’m not the only one: I’ve just received a copy of a lawsuit filed by Avenue Media, complaining that Direct Revenue is “systematically deleting Avenue Media’s Internet Optimizer without users’ knowledge or consent.” Indeed, in my November 17 testing, I found that software installed on my PC by ABetterInternet (a product name used by Direct Revenue) received the following instructions from its targeting server, calling for the removal of Avenue Media’s Internet Optimizer:
POST /bi/servlet/ThinstallPre HTTP/1.1
…
Host: thinstall.abetterinternet.com
excerpted to show only removal
code targeting Internet Optimizer
HTTP/1.1 200 OK
Date: Wed, 17 Nov 2004 15:31:00 GMT
Server: Apache/2.0.46 (Red Hat)
Content-Length: 3881
Connection: close
Content-Type: text/xml
<install><action type=”KillProc”>
<proc exe=”optimize.exe” />
</action>
(in usual Windows .INF format)
…
<action type=”installINF”>
<inf section=”DefaultInstall”>
…
[DefaultInstall] …
DelReg=RegistryEntries
DelFiles=ProgFiles,systemFiles
…
[RegistryEntries] …
HKLM,SOFTWARE\Microsoft\Windows\CurrentVersion\Run,”Internet Optimizer”
…
[ProgFiles]
Internet Optimizeractalert.exe,,,1
Internet Optimizeroptimize.exe,,,1
Internet Optimizerupdateactalert.exe,,,1
In my testing, Direct Revenue’s software acts on these instructions — stopping the optimize.exe task (Internet Optimizer’s main program), then deleting the associated registry entries and program files. So I think Avenue Media is correct as to the basic facts of what’s happening. Conveniently, in tests beginning on November 17, I even made videos showing Internet Optimizer’s software being deleted — files eerily disappearing as Direct Revenue’s software deleted Internet Optimizer along with other targeted programs.
How do I happen to have records, logs, and even videos of events occurring several weeks ago? As it turns out, both Internet Optimizer and Direct Revenue were unwanted additions to my test PC: Both were installed through security holes, much like the installations I documented in my Who Profits from Security Holes? write-up and video last month. I’ve been making more such videos — roughly one a day for the past few weeks. So I’ve repeatedly seen Direct Revenue removing Internet Optimizer.
In my security-hole videos, I never saw nor accepted any Direct Revenue license. So, at least as to me, Direct Revenue cannot convincingly cite its EULA to defend its removal of Internet Optimizer. (See also my recent analysis of Gator’s EULA.) However, my test PC became noticeably faster after Direct Revenue removed other unwanted programs that had been installed through security holes. So, for some consumers, Direct Revenue’s removal of competitors’ programs may offer a useful if surprising benefit. (Compare: Radlight removing Ad-Aware, without any apparent benefit to consumers.)
Case documents: Avenue Media v. Direct Revenue
As promised: Internet Optimizer’s case documents, alleging claims under the Computer Fraud and Abuse Act as well as for tortious interference with economic relations:
Complaint: Avenue Media, N.V. v. Direct Revenue LLC, BetterInternet LLC (PDF)
Memorandum in Support of Temporary Restraining Order (PDF)
Declaration of Moses Leslie (PDF)
Response by Direct Revenue (PDF) and supporting declaration of Joshua Abram (PDF)
Avenue may be suffering from wrongful behavior by Direct Revenue, but note that Avenue has problems of its own. In my tests, Avenue’s software (like Direct Revenue’s) was installed without any notice or consent whatsoever. (Again, I have video proof.) However installed, Internet Optimizer’s primary function is to show extra advertising, primarily by replacing web browser error messages with its own ads — not a feature most users request. In addition, Internet Optimizer’s EULA admits to tracking web sites visited and keywords searched. Finally, Doxdesk reports that Internet Optimizer has (or recently had) security holes that risk unauthorized installation of other software.
Update (February 8, 2005): Avenue Media and Direct Revenue have reportedly reached a settlement. No money will change hands, but the companies have agreed to no longer disable each other’s software.
Removing competitors’ programs is not Direct Revenue’s only controversial activity. Direct Revenue’s core business is showing extra pop-up ads. Which ads? Covering which sites? Early next year, I expect to release a report detailing some of the advertisers supporting Direct Revenue, and showing some ads Direct Revenue targets at certain web sites. Advance access available by request.
I also plan to present the sensitive information sent by Direct Revenue to its servers. In recent testing, I’ve seen Direct Revenue collect each user’s ethernet address or “MAC address” — a unique identifier permanently associated with each network card (i.e. with each computer). Direct Revenue also transmits users’ Windows product IDs — of particular interest due to their use in Microsoft’s product activation system.
I have recently observed that Direct Revenue tracks the .EXE names of all running tasks, specifically checking for installations of certain competing programs (including Gator and 180solutions) and for certain spyware-removal programs (including Ad-Aware and PestPatrol). Direct Revenue checks for these programs in the same way it checks for Internet Optimizer — suggesting that Direct Revenue might also target some or all of these programs for automatic deletion, just as it automatically deleted Internet Optimizer in the log shown above. That hypothesis is more than speculative: My November videos and packet logs show Direct Revenue deleting not just Internet Optimizer but also ActAlert/DyFuCa, EliteToolbar, and others.
Finally, note that Direct Revenue recently received $20 million of funding from Insight Venture Capital Partners, as well as $6.7 million from Technology Investment Capital Corp (TICC).
Gator’s EULA Gone Bad
Gator has recently taken steps to portray itself as a model citizen among what it calls “adware” companies. Gator proudly announced support for California’s new anti-spyware law. (But see my criticism of the law as ineffective.) Earlier this year, Gator hired a former FTC staff attorney to serve as Gator’s chief privacy officer, participated (PDF) in the FTC‘s spyware workshop, and even joined CDT‘s “consumer software working group” committee. (See recommendations document (PDF) signators list, final page.)
Has Gator turned over a new leaf? For insight, I turned to Gator’s license agreements, to see how Gator currently presents itself to ordinary users.
Table of Contents
Prohibition on automated removal tools
Prohibition on investigating transmissions
License formatting: headings, search, print
What the license doesn’t say
It’s not often that I sit down to read Gator’s license agreements. At 5,936 words, the license stretches to 63 on-screen pages as presented by the current Kazaa installer (bundling Gator). (See screen-shots of the Gator license as presented in June 2004, then requiring 56 on-screen pages.) Here are some notable sections of the license:
Prohibition against automated removal tools
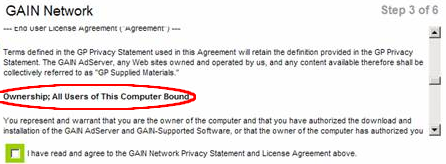
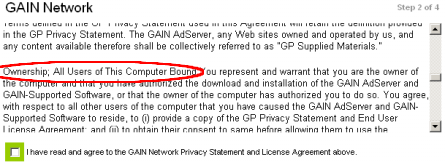
Nearly three thousand words into its license, Gator proclaims:
You agree that you will not use, or encourage others to use, any unauthorized means for the removal of the GAIN AdServer, or any GAIN-Supported Software from a computer.”
Gator proceeds to list the “authorized means” for removing Gator — prominently failing to authorize use of popular tools, such as Ad-Aware, Spybot, and Web Sweeper, which millions of users count on to remove unwanted software from their PCs.
In recent press releases, Gator has claimed to favor “consumer … choice” and has argued that what occurs on users’ computers is “users’ choice.” So long as consumers are (supposedly) choosing to run Gator software, Gator vigorously defends user choice. But when a consumer chooses to use third-party software to remove Gator, Gator instead specifically prohibits that choice.
If Gator were easy to uninstall, users might not need to resort to third-party removal programs. But Gator makes its software hard to remove. Browse to Add/Remove Programs on a computer with Gator installed, and there’s often no entry for Gator. Instead, users are required to identify, find, and remove all programs that bundle Gator, and only then is Gator’s software designed to uninstall. This unusual removal procedure — unique among all programs I’ve ever encountered — makes Gator difficult for users to remove.
Removing Gator becomes even harder, using Gator’s official removal procedure, as a result of Gator’s cross-promotion of its various products. After a user receives Gator’s GAIN advertising-display software, Gator often shows pop-ups that encourage installation of other Gator programs, such as clock synchronizers and weather monitors. As a result, many users run multiple “Gator-supported” applications, each of which must be separately identified and removed in order to use Gator’s official removal procedure. Facing Gator’s lengthy and complicated removal procedure, it’s no wonder many users look to third-party removal programs for help.
Prohibition against viewing or recording what Gator software says about its users over users’ own Internet connections
About four thousand words through its license, Gator demands:
“Any use of a packet sniffer or other device to intercept or access communications between GP and the GAIN AdServer is strictly prohibited.”
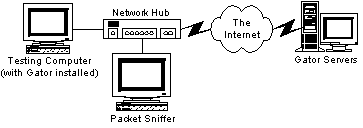 Network structure for monitoring
Network structure for monitoring
As shown in the diagram at right, network monitors (or “packet sniffers”) are devices that inspect and report Internet transmissions from a local network. Sniffers are the ordinary and usual method of observing what data test computers send to and from the Internet. The transmissions from Gator’s software to its servers are sent from users’ PCs over users’ own Internet connections. But according to Gator’s license, users cannot take steps to observe what data Gator is collecting about them. Users must take Gator at its word as to Gator’s privacy policy, because users would violate Gator’s license agreement if they monitored Gator’s transmissions to confirm what data Gator sends.
Beyond constraining ordinary users, this license provision also blocks legitimate academic research. In “Measurement and Analysis of Spyware in a University Environment” (PDF), three University of Washington computer scientists used packet sniffers to measure the prevalence of Gator software and to detect security holes in Gator software. If Gator’s then-current license was as quoted above, their research would seem to constitute a violation. My own past work might also be prohibited, because I have used packet sniffers in multiple projects testing Gator software: In comments to the FTC (PDF, pages 4-6), I reported the precise personal information transmitted by Gator. I previously built a system to report what ads Gator shows where, simply by repeating the format of requests made by ordinary Gator software. (See Documentation of Gator Advertisements and Targeting.)
Gator might be pleased to stop users and researchers from knowing the personal information Gator transmits, tracking the prevalence of Gator’s software, finding Gator’s security holes, and analyzing what ads Gator shows where. But should Gator be able to achieve these results merely by adding an extra sentence to its license agreement?
 A Claria drive-by download prompt — allowing the user to press ‘Yes’ and have software installed, without first seeing Claria’s license agreement.
A Claria drive-by download prompt — allowing the user to press ‘Yes’ and have software installed, without first seeing Claria’s license agreement.
It’s not always easy to read Gator’s license. For one, some Gator ActiveX “drive-by download” installers include defective license agreements. I have repeatedly observed (and have preserved in video recordings) Gator installers where a user’s specific request for the Gator license (by clicking on the “after accepting our agreements…” hyperlink) yields no license at all. In other instances, the license request yields only the first few lines of a license, presented in a web page that lacks scroll bars with which to view the rest of the license. In these circumstances, even users who specifically ask for Gator licenses do not receive them.
The Kazaa bundle also makes it difficult to review Gator’s license. For example, the current license agreement is longer than ever: The license takes 63 screens to display, compared to 56 in my screenshots of earlier this year.
 The ‘printable version’ link, present in old Kazaa installers but no longer available.
The ‘printable version’ link, present in old Kazaa installers but no longer available.
Gator has also made its license less accessible by removing one-click access to the full text of the license. In the past, Kazaa’s Gator install screen included a “Printable Version” link (see inset at right and screenshot) which opened the license in a separate text viewer, complete with print, search, and resize functions. However, the “Printable Version” link is omitted from Kazaa’s current Gator installer (screenshot). Users wanting a printable version of Gator’s license have no obvious direct way to get it.
In addition, Gator’s current license merges section headings with body text, making the license harder to read. Gator’s license (as shown by Kazaa earlier this year) previously included nearly three dozen section headings, each using bold type and/or blank lines to help separate and identify a license section. The left screen shot below depicts one such heading. But the current license (right image below) eliminates all but one instance of bold type and also omits the line breaks following all but four (of 37) section headings. With Gator’s section headings effectively indistinguishable from the license text, even determined users can’t readily find the sections of particular interest.
|
Representative image from Gator’s June 2004 Kazaa installer |
The corresponding section of today’s Gator/Kazaa installer |
In 5,900+ words of text, there’s no shortage of space for Gator to describe itself in terms that ordinary users can understand. But a search of the license shows Gator has failed even to mention the words and phrases most users associate with Gator’s products.
Although Gator is in the pop-up advertising business, Gator uses these terms infrequently. The license first mentions the word “pop-up” at page 18 of 63. The phrase “pop-up ad” appears only once in the license, at page 27, where the phrase is used to refer to pop-up surveys from Gator’s Feedback Research division. Gator’s pop-up ads are repeatedly described not as “advertisements” but, euphemistically, as “pop-up windows” and “floating images on top other windows” (sic). Nowhere in Gator’s license does Gator use the phrase “pop-up ad” to refer to the Gator pop-ups that cover web sites with advertisements for the sites’ competitors.
Gator calls itself an “adware” company, while critics often call Gator spyware. But neither “adware” nor “spyware” appears anywhere in Gator’s license agreement.
I don’t claim to have found all the nuggets of controversy in Gator’s license agreement; there are surely additional problematic sections. Send suggestions for addition to this page.
Who Profits from Security Holes? updated November 24, 2004
I’ve written before about unwanted software installed on users’ computers via security holes. For example, in July I mentioned that 180solutions software was being installed through Internet Explorer vulnerabilities. (See also 1, 2, 3) More recently, researchers Andrew Clover and Eric Howes (among others: 1, 2) have described increasing amounts of unwanted software being installed through security holes.
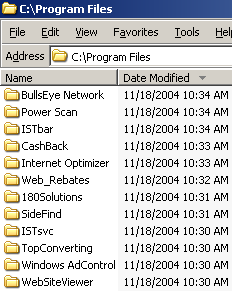 Malware installed through a single security exploit
Malware installed through a single security exploit
How bad is this problem? How much junk can get installed on a user’s PC by merely visiting a single site? I set out to see for myself — by visiting a single web page taking advantage of a security hole (in an ordinary fresh copy of Windows XP), and by recording what programs that site caused to be installed on my PC. In the course of my testing, my test PC was brought to a virtual stand-still — with at least 16 distinct programs installed. I was not shown licenses or other installation prompts for any of these programs, and I certainly didn’t consent to their installation on my PC.
In my testing, at least the following programs were installed through the security hole exploit: 180solutions, BlazeFind, BookedSpace, CashBack by BargainBuddy, ClickSpring, CoolWebSearch, DyFuca, Hoost, IBIS Toolbar, ISTbar, Power Scan, SideFind, TIB Browser, WebRebates (a TopMoxie distributor), WinAD, and WindUpdates. (All programs are as detected by Ad-Aware.) I have reason to believe that numerous additional programs were also installed but were not detected by Ad-Aware.
See a video of the installations. The partial screen-shot at left shows some of the new directories created by the security exploit.
Other symptoms of the infection included unwanted toolbars, new desktop icons (including sexually-explicit icons), replacement desktop wallpaper (“warning! you’re in danger! all you do with computer is stored forever in your hard disk … still there and could broke your life!” (s.i.c.)), extra popup ads, nonstandard error pages upon host-not-found and page-not-found error conditions, unrequested additions to my HOSTS file, a new browser home page, and sites added to my browser’s Trusted Sites zone.
I’ve been running similar tests on a daily basis for some time. Not shown in the video and screen-shot above, but installed in some of my other tests: Ebates Moe Money Maker, EliteToolBar, XXXtoolbar, and Your Site Bar.
Installation of 180solutions software through security holes is particularly notable because 180 specifically denies that such installations occur. 180’s “privacy pledge” claims that 180 software is “permission based” and is “programs are only downloaded with user consent and opt-in.” These claims are false as to the installation occuring in the video linked above, and as to other installations I have personally observed. Furthermore, 180’s separate claim of “no hiding” is false when 180 software is installed into nonstandard directories (i.e. into C:Windows rather than a designated folder within Program Files) and when 180 software is installed with a nonstandard name (i.e. sais.exe) rather than a name pertaining to 180’s corporate name or product names.
What’s particularly remarkable about these exploits is that the bad actors here aren’t working for free. Quite the contrary, they’re clearly expecting payment from the makers of the software installed, payments usually calculated on a per-install basis. (For example, see a 2003 message from 180solutions staff offering $0.07 per installation.) By reviewing my network logs, I can see the specific “partner” IDs associated with the installations. If the installers want to get paid, they must have provided accurate payment details (address, bank account number, etc.) to the makers of the programs listed above. So it should be unusually straightforward to track down who’s behind the exploits — just follow the money trail. I’m working on passing on this information to suitable authorities.
Note that the latest version of Internet Explorer, as patched by Windows XP Service Pack 2, is not vulnerable to the installations shown in my video and discussed above.
Cookie-Stuffing Targeting Major Affiliate Merchants
Certain affiliate web sites use pop-ups, pop-unders, IFRAMEs, JavaScript, and other methods to claim affiliate commissions on users purchases from affiliate merchants, even if users do not click on affiliates’ links to the merchants. This page documents selected affiliates using these practices and selected merchants suffering from these practices.
Overview & Summary
Affiliate tracking systems are intended to pay commissions to independent web sites (“affiliates”) when users click through these sites’ links to affiliate merchants. Merchants are not intended to pay commission when users merely visit affiliates’ sites. Instead, commission ordinarily only becomes payable in the event that a user 1) visits an affiliate’s site, 2) clicks through an affiliate link to a merchant, and 3) makes a purchase from that merchant.
However, some affiliates use “cookie-stuffing” methods to cause affiliate merchants’ tracking systems to conclude that a user has clicked through a tracking link (and to pay commissions accordingly) even if the user has not actually clicked through any such link. If the user subsequently makes a purchase from that merchant — immediately, or within the “return days” period specified by the merchant’s affiliate program — the affiliate then receives a commission on the user’s purchase.
This page presents the incentives that have allowed cookie-stuffing to continue, and captures selected examples of cookie-stuffing. See also the Affiliate Fraud Information Lookup, reporting of the number of observations Wesley Brandi and I have gathered in ongoing high-volume tests for cookie-stuffing.
Groups Affected by Cookie-Stuffing
Affiliate Networks Benefit from Cookie-Stuffing
Affiliate merchants ordinarily pay their affiliate networks a percentage of all affiliate revenues passing through the network. For example, Commission Junction’s public pricing list reports that CJ charges a merchant 30% of all amounts to be paid to affiliates. (In other words, if a merchant sells $1,000,000 of merchandise and pays a 5% affiliate commission, then it must pay $50,000 of commission to its affiliates. It must further pay 30% of $50,000, or $15,000, to Commission Junction.) As a result, in the first instance, affiliate networks benefit from cookie-stuffing. Such cookie-stuffing increases the total volume of sales flowing through affiliate networks, and increases the affiliate commissions on which, for example, CJ can charge a 30% fee.
Set against this short-run incentive is the long-term problem that if affiliate networks fall greatly in value to merchants, or if affiliate networks are perceived to facilitate fraud, then merchants may no longer be willing to pay affiliate commissions and affiliate network fees. But in the short run, affiliate networks benefit from more money flowing through their networks.
To date, affiliate networks have failed to aggressively pursue, stop, and punish those affiliates using cookie-stuffing. Indeed, LinkShare has repeatedly granted a $15,000 award to affiliates later found to be using cookie-stuffing. In each instance LinkShare subsequently withdrew the award after pressure from affiliates, merchants, and others. (See MediaPost coverage.) LinkShare’s repeated awards to affiliates using cookie-stuffing reveal that this technique extends to large affiliates and to well-regarded affiliates.
That said, affiliate networks’ black-letter rules generally officially prohibit cookie-stufing. For example, Commission Junction’s Publisher Service Agreement states that an affiliate publisher “may earn financial compensation … for transactions … made from such publisher’s web site … through a click made by a visitor … through an Internet connection (link) to a web site.” In all the examples set out below, no such click occurred, and therefore no commission is fairly earned given the limitations set out in the PSA.
Affiliate Merchants Suffer from Cookie-Stuffing
Affiliate merchants suffer financially from cookie-stuffing. Cookie-stuffing causes merchants to pay commissions that, according to program rules, they need not pay. Cookie-stuffing also causes merchants to pay commissions to the wrong affiliates — to affiliates who never caused an actual user click-through — which is likely to reduce the quality and effort of affiliates participating in the merchant’s program.
Cookie-Stuffers Profit from Cookie-Stuffing
Cookie-stuffing apparently proves profitable for those who do it. Suppose an affiliate ordinarily has a 10% click-through rate from its site to its merchants. The affiliate ordinarily receives affiliate commission only if a purchase is made by one of the 10% of users who clicks through the affiliate’s link. In contrast, by cookie-stuffing, the affiliate can claim commissions from any purchases made by the entire 100% of the affiliate’s visitors.
Rule-Following Affiliates Suffer from Cookie-Stuffing
Rule-following affiliates suffer from cookie-stuffing. For one, rule-following affiliates’ cookies may be overwritten by cookie-stuffers. Suppose a user clicks to affiliate site A, a rule-follower not using cookie-stuffing, and clicks through A’s link to a given merchant. The next day, the user visits affiliate site B, a rule-breaker using cookie-stuffing as to the same merchant site. Using cookie-stuffing, site B sets an affiliate tracking cookie that overwrites A’s cookie. If the user subsequently makes a purchase from the merchant, the affiliate commission will be paid to B, not A.
Rule-following affiliates also suffer from cookie-stuffing because cookie-stuffing encourages merchants to cut their commission rates. Without cookie-stuffing, merchants would be paying commissions on fewer orders. At least some merchants would likely then choose to increase commission paid on each order.
Specific Examples of Cookie-Stuffing
This section links to my research and testing, showing cookie-stuffing targeting major affiliate merchants. In initial reporting, I have focused on cookie-stuffing targeting merchants CJ designates as “featured” and on merchants who participate in discussion fora on ABestWeb.
The table below gives “clear-cut” examples of cookie-stuffing — affiliate HTML code that clearly shows intention to set affiliate cookies without a user clicking through any affiliate link.
| Merchant | Cookie-Stuffing Affiliate | Date | Notes |
| Amazon (an independent merchant) | Avxf (qufrho-20) | 10/6/08 | Broken IMG loaded within forum page. Details and video. |
| Amazon (an independent merchant) | consumernow.com (jumpondealscom) | 11/6/04 | Obfuscation via a redirect. Details and video. |
| Amazon (an independent merchant) | Bannertracker-script | 2/27/12 | JavaScript invisibly inserted into multiple independent sites via web server hacking. 200+ affiliate IDs in use. Details. |
| Amazon (an independent merchant) | Imgwithsmiles | 5/2/12 | Flash-based stuffing syndicated through Google AdSense display ad network. 49+ affiliate IDs in use. Details. |
| Argos (a CJ Advertiser) | Eshop600 (3910892) | 1/30/12 | Encoded JavaScript and invisible IMG. 26 cookies stuffed at once. Details. |
| Barnes & Noble (a CJ Featured BFAST Advertiser) | dailyedeals.com (BFAST 26682568) | 11/4/04 | Misleading JavaScript comments. Details and video. |
| Buy.com (a CJ Advertiser) | Couponcodesmall (2705091) | 10/5/08 | Invisible IFRAME. Details and video. |
| Cooking.com (a LS Selected Merchant) | dailyedeals.com (FZOkC4w7rNM) | 11/6/04 | Misleading JavaScript comments. Details and video. |
| Crucial.com (a CJ Featured Vantage Advertiser) | dailyedeals.com (340672) | 11/2/04 | Details and video. |
| Dell (a LS Selected Merchant) | jumpondeals.com (HAHu6s1Hzp4) | 11/5/04 | Obfuscation via a redirect. Details and video. |
| Dentalplans (an ABestWeb CJ merchant) | consumernow.com (517038) | 11/6/04 | Obfuscation via a redirect. Details and video. |
| Drugstore.com (a LS Selected Merchant) | dailyedeals.com (FZOkC4w7rNM) | 11/6/04 | Misleading JavaScript comments. Details and video. |
| Eastwood (an ABestWeb CJ merchant) | aboutdiscounts.com (1311826) | 11/4/04 | SCRIPT after /HTML. Details and video. |
| eVitamins (an ABestWeb CJ merchant) | couponvine.com (465743) | 11/4/04 | Two-step JavaScript. Details and video. |
| Folica (a CJ merchant) | ahugedeal.us (568228) | 11/8/04 | Details and video. |
| Folica (a CJ merchant) | ahugedeal.com (568228) | 10/25/05 | Still occurring with same affiliate ID, 11+ months after prior reporting. Obfuscation via a redirect. Details and video. |
| FunToCollect (an ABestWeb CJ merchant) | specialoffers.com (306244) | 11/6/04 | Obfuscation via a redirect. Details and video. |
| Globat (a CJ merchant) | coupon-monkey.com (1446676) | 11/8/04 | /CLICK loaded in IMG tag. Details and video. Note: Coupon-monkey claims cookie-stuffing was accidental. Details. |
| HostGator (an independent merchant) | Avxf (dsplcmnt01) | 10/6/08 | Broken IMG loaded within forum page. Details and video. |
| HSN (a CJ Featured BFAST Advertiser) | coupons-coupon-codes.com (BFAST 38772000) | 11/4/04 | Obfuscation via external JavaScript and redirect. Details and video. |
| iPowerWeb (a CJ BFAST merchant) | bids2buy.com (1525933) | 11/6/04 | Details and video. |
| Irv’s Luggage (an ABestWeb CJ merchant) | edealinfo.com (600263) | 11/4/04 | IFRAME. Details and video. |
| JCWhitney (an ABestWeb CJ merchant) | consumernow.com (517038) | 11/6/04 | Obfuscation via a redirect. Details and video. |
| LaptopsforLess (an ABestWeb CJ merchant) | find-coupon.com (1525933) | 11/4/04 | Popup. Details and video. |
| Match.com (a CJ Featured Vantage Advertiser) | asmartcoupon.com (1515738) | 11/4/04 | /CLICK loaded in IMG tags. Details and video. |
| MLB.COM (a CJ Featured Vantage Advertiser) | edealinfo.com (600263) | 11/4/04 | IFRAME. Details and video. |
| Napster (a CJ front-page Featured Advertiser) | coupons-online-coupon.com (1167113) | 11/4/04 | Popup. Details and video. |
| Netzero (a CJ Featured Vantage Advertiser) | consumernow.com (517038) | 11/4/04 | Obfuscation via a redirect. Details and video. |
| Orbitz (a LS Selected merchant) | thewinnersclub.net (HAHu6s1Hzp4) | 11/8/04 | Obfuscation via a redirect. Details and video. |
| Oreck (an ABestWeb CJ merchant) | 1couponstop.com (517038) | 11/4/04 | Obfuscation via a redirect. Details and video. |
| Overstock.com (an ABestWeb LS merchant) | dailyedeals.com (FZOkC4w7rNM) | 11/5/04 | Misleading JavaScript comments. Details and video. |
| PetcareCentral (an ABestWeb CJ merchant) | aboutdiscounts.com (276460) | 11/4/04 | SCRIPT after /HTML. Details and video. |
| Priceline (a CJ BFAST merchant) | findsavings.com (40001021) | 11/7/04 | Details and video. |
| RapidSatellite (an ABestWeb CJ merchant) | smartqpon.com (979227) | 11/4/04 | Details and video. Details and video. |
| Relaxtheback.com (a LS Selected Merchant) | office-coupons-online.com (g/KOq4zlIIk) | 11/6/04 | Details and video. |
| Shoes.com (an ABestWeb CJ merchant) | ultimatecoupons.com / webbuyingguide.com (1417434) | 11/4/04 | Cookie tracking of popunder triggering. Details and video. |
| ShopNBC (a CJ Featured BFAST Advertiser) | ultimatecoupons.com / webbuyingguide.com (BFAST 38954339) | 11/4/04 | IFRAME. Details and video. |
| SkinStore.com (a CJ BFAST merchant) | discount-coupons-online.com (568228) | 11/6/04 | Details and video. |
| Spafinder.com (a LS Merchant) | ultimatecoupons.com / webbuyingguide.com (OEu024dtHXs) | 11/6/04 | JavaScript URL variable. Details and video. |
| Toshiba (a CJ front-page Featured Advertiser) | consumernow.com (517038) | 11/4/04 | Obfuscation via a redirect. Details and video. |
| TigerDirect.com (an ABestWeb CJ BFAST merchant) | findsavings.com (39104038) | 11/5/04 | Details and video. |
| Travelocity (a CJ BFAST Selected merchant) | xpcoupons.com (40031581) | 11/8/04 | IFRAME. Placed after /BODY. Details and video. |
The table below gives additional examples of cookie-stuffing. In these examples, I see insufficient basis to determine whether the affiliate intended to set affiliate cookies without a user clicking through any affiliate link. Nonetheless, that is the net effect of the examples linked below.
| Merchant | Cookie-Stuffing Affiliate | Date | Notes |
| DentalPlans (an ABestWeb CJ merchant) | savings-center.com | 11/4/04 | FRAME. Details and video. |
| FunToCollect (an ABestWeb CJ merchant) | goodbazaar.com | 11/4/04 | FRAME with META tags. Details and video. |
| JCWhitney (an ABestWeb CJ merchant) | a2zrewards.com | 11/4/04 | FRAME with META tags. Details and video. |
| Travelocity (a CJ BFAST merchant) | couponmountain.com | 11/8/04 | Redirect with META tags, broken BACK button. Details and video. |
Because LinkShare’s compliance and quality problems are already well-known (e.g. as described above, as to LinkShare’s repeated Titanium Award missteps), the listing above focuses primarily on Commission Junction merchants.
Last Updated: May 8, 2012
Grokster and Claria Take Licenses to New Lows, and Congress Lets Them Do It
I’ve recently been looking at the unwanted software installed by Grokster (a peer-to-peer filesharing program). Eric Howes has documented Grokster’s exceptionally large bundle, which includes Claria, 411 Ferret/ActiveSearch, AdRoar, Altnet/BDE, BroadcastPC, Cydoor, Flashtrack, MyWay/Mybar, SearchLocate/SideBar, Topsearch, TVMedia, VX2/ABetterInternet, Browser Hijack, two different TopMoxie programs (branded by WebRebates), and several other programs not yet identified.
These programs, in combination, place a major burden on users’ computers: Loading and running so many extra tasks leaves less memory, less bandwidth, and less CPU time for whatever users actually want to do. My lab PCs are fast and well-maintained, but installing Grokster and its bundle makes them sluggish and hard to use. Worse, it’s hard to undo the damage Grokster and its partners cause: Eric also tracks, in unprecedented detail, how even the newest spyware removal applications can’t get rid of all the programs Grokster installs. It’s a mess, Eric’s site explains, and he’s surely right.
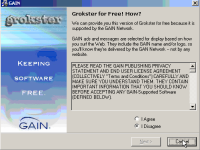
But as it turns out, the situation is even worse than Eric realized. As Eric explains, Grokster installs lots of junk if a user presses Accept. However, Grokster also installs software even if the user presses Cancel! That’s right: If a user has second thoughts after seeing the long license agreements, and if the user decides to press Cancel, Grokster’s installer nonetheless installs SearchLocate/SideBar and TVMedia. See the screen-shots below, taken from my video (WMV, 1MB) of the install process. (For best viewing, watch video in full-screen mode.)
Equally outrageous are the extraordinarily lengthy license agreements Grokster and its partners ask users to accept. First comes a Claria license agreement that takes, by my count, 120 distinct screens (119 presses of the page-down key) to view in full. As shown in the Grokster installer, Claria’s license has grown to an incredible 6,645 words. So Claria’s current license is 43% longer than the US constitution — before we count the nine separate web pages Claria’s license references, some of them quite lengthy, but which Claria nonetheless claims are “incorporated by reference.” Furthermore, Claria’s license is growing rapidly: When I prepared screen-shots of Claria’s license, as shown by Kazaa in June 2004, the license was 5,541 words long. If Claria’s license continues to grow by 20% every four months, it will be 11,500 words long in October 2005, and 34,300 words long in October 2007. Maybe Claria’s lawyers get paid by the word.
And it gets worse: Grokster installs other programs, with their own licenses, and Grokster shows these many licenses en masse in a subsequent screen. These licenses appear in a text box that, for whatever reason, doesn’t let me to copy its text to the clipboard. So I can’t know the precise word count of the licenses in this second box. But I do know it took 278 page-downs to view the entire license.
That makes a total of 398 page-downs for any user who wants to know what lies in store upon installing Grokster. 398!
This past week, the US House of Representatives passed two bills that purport to address the spyware problem. Would they do anything about Grokster’s outrageous activities?
Goodlatte‘s H.R.4661 prohibits unauthorized software installation — but only under specific, narrow circumstances. I can’t immediately say that SearchLocate/SideBar and TVMedia are used in furtherance of a Federal criminal offense, so Sec.2.(a) is inapplicable. And I can’t say that the programs intentionally obtain or transmit personal information with the intent to defraud, injure, or cause damage. Surely the programs’ authors would deny any such intent. So Sec.2.(b) is inapt too. Looks like Goodlatte’s bill wouldn’t help.
Bono‘s H.R. 2929 does prohibit the unauthorized software installation. Sec.2.(a)(4)(A) specifically bans installing software when a user declines installation. Score one for the good guys.
But suppose Grokster ended the truly outrageous installation of software even when users press Cancel, instead installing its bundle only when users press Accept. (Grokster will more than likely make this change after reading my article.) Then Grokster would be, I fear, substantially compliant with H.R.2929.
For 2929’s purposes, it doesn’t matter that Grokster installs so much software that it essentially ruins even an above-average PC. The bill’s Sec.3. approves of the installation of fifteen programs, or a hundred and fifteen, so long as the user is first shown a single notice that warns “This program will collect information about Web pages you access and will use that information to display advertising on your computer. Do you accept?’ Or, thanks to a recent revision to the bill, the installer can show some other text, so long as it is “substantially similar,” but even if it is more complicated, more confusing, or harder to understand.
I worry that Grokster can and will include the brief disclosure 2929 specifies, or an alternative text that makes the installation sound even more unobjectionable. Then all too many users will be tricked into accepting Grokster’s massive software bundle, and they will find their PCs grind to a halt under the load Grokster and its partners impose. Users will be running Bono-certified software, 100% compliant with relevant law (should Bono’s bill in fact become law). But their computers will be nearly useless nonetheless.
If I were revising Bono’s bill, I’d seek to tighten its requirements. I certainly wouldn’t permit watered-down “substantially similar” disclosures. I’d also prohibit the installation of a bundle of software, where the user requested only a single program, if that bundle has significant adverse effects on the speed and reliability of a typical computer, and if that bundle has no substantial relationship to the software the user initially requested. For bundled programs that show advertising, I’d require that the installation provide a sample of each kind of advertisement to be shown, and I’d require that the installation disclose the typical frequency of ad displays. In short, there are lots of creative ways to tighten the language, so that programs can’t satisfy the bill’s requirements while continuing to trick users into unwanted installations.
Instead, 2929 takes a narrower approach — admittedly stopping a class of outrageous behaviors, but letting all too many continue. Given the bill’s preemption of tougher state laws, this is legislation that, far from stopping spyware, in many respects makes the spyware problem worse.
Can we count on the Senate to close the loopholes in the bills as passed? News coverage suggests that these bills are a done deal already. And Congress has enacted weak legislation before (e.g. CAN-SPAM). So I’m not holding my breath.
California’s Toothless Spyware Law
Yesterday Governor Schwarzenegger signed into law SB 1436 (“Computer Spyware”), a California bill that speaks to certain programs installed on users’ computers. The bill admittedly speaks to programs that trick users, harm users, and take advantage of users. So why don’t I support it?
SB1436 prohibits a number of activities. It bans, for example, transmitting computer viruses from a users’ computers (22947.3(a)(1)), using a computer as part of a denial of service attack ((a)(3)), and presenting an option to decline installation of software when selecting that option will in fact cause software to be installed nonetheless ((c)(1)). These are surely bad actions. But they’re all prohibited under existing law — fraud, unfair trade practice, computer fraud and abuse act, etc. When investigators, lawyers, and researchers have tracked down bad actors using these methods in the past, they’ve proceeded with suit, with considerable success. (See e.g. Melissa virus writer’s jail sentence.) So we don’t need SB1436 to address these outrageous activities.
 A Claria drive-by download prompt — allowing the user to press ‘Yes’ and have software installed, without first seeing Claria’s license agreement.
A Claria drive-by download prompt — allowing the user to press ‘Yes’ and have software installed, without first seeing Claria’s license agreement.
In contrast, SB1436 fails to speak to the truly controversial activities — many of them arguably “borderline” — that have actually been used by major players in the spyware space, whose installed user counts now reach into the tens of millions. Consider Claria’s 5,500 word license agreement. As presented in Kazaa’s installer (screenshots), Claria’s license is 20% longer than the US Constitution, and it requires 56 on-screen pages to view in full. Or, consider Claria’s drive-by installer (screenshot), where a user can press “Yes” without ever even seeing Claria’s license. More recently, Claria’s drive-bys have begun to show users the Claria license — but only after the user presses Yes, and only after the software is installed! What should we make of such installation practices? Has a user really “accepted” Claria’s software when the user receives unhelpful, confusing, and/or untimely disclosures? Even if the user is a minor? Even if the user mistakenly thought Claria’s software was necessary to view the web page that triggered the drive-by? Some courts may think that pressing “Yes” indicates assent — no matter the circumstances, no matter how one-sided the terms presented, and for that matter even if the terms weren’t actually presented (but were merely linked to). But I don’t think that’s a necessary conclusion, given the length and presentation of the supposed agreement.
SB1436 had an opportunity to address these deceptive installation tactics by clarifying standards for notice and consent. Indeed, the first draft of SB1436 (dated February 19, 2004) addressed Claria’s tactics directly: “‘Spyware’ means an executable program that automatically … transmits to the provider … data regarding computer usage, including … which Internet sites are or have been visited by a user” — exactly what Claria does. The February draft went on to set out various requirements and disclosure duties, even including a minimum font size for disclosure. That’s not to say the February bill was perfect — certainly there was more fine-tuning to be done. But it sought to establish disclosure duties for all companies transmitting information about users’ online browsing — not just a few outrageous outliers who send viruses.
Unfortunately, SB1436’s initial comprehensive approach somehow got lost between the February draft and the August revisions. A recent RedHerring article claims the bill was “gutted” by “the well-heeled and influential online advertising lobby.” Claria’s chief privacy officer recently stated that he had “met with the staffs of members who have proposed legislation” — though not mentioning any special efforts to modify the bill. Whatever Claria’s role, even a quick reading shows that the revised bill won’t affect Claria’s current practices.
Meanwhile, Claria gets to go on record not only supporting the law, but perhaps even complying with it from its first day in effect. Claria can now claim the implicit endorsement of California law: After all, if California passed a spyware law, and Claria complies, then (the logic goes) Claria must be a legitimate business that consumers and advertisers should happily do business with. But the truth is not so simple: Claria’s deceptive installation methods continue, tricking tens of millions of users into receiving Claria software without truly understanding what they’re getting into.
A better spyware bill would address the subtleties of Claria’s methods — would address lengthy, confusing licenses, and licenses shown only after supposed consent. Interestingly, some of the pending federal legislation speaks to disclosure requirements for programs like Claria. The federal bills are far from perfect. But they at least seek to address the harms, like Claria, that actually plague millions of users day in and day out. More on the proposed federal legislation next month.
Pick-Pocket Pop-Ups
I’ve been writing for months — years! — about unwanted programs, installed on users’ PCs, that show users extra pop-up ads. There’s been lots to write about: The actual ads shown (WhenU’s and Gator’s), whether users grant meaningful consent (especially in the face of lengthy licenses), privacy (and possible privacy violations), and online marketing methods (like search engine spamming) sometimes used by companies in this space.
Today I present research about another problem, quite distinct from pop-ups: Programs that tamper with affiliate commissions. Call them stealware, thiefware, or even “pick-pocket pop-ups” (a term recently coined by Kenn Cukier), but their core method is surprisingly simple: Stealware companies join the affiliate networks that merchants operate — networks intended to pay commissions to independent web sites that recommend the merchants to their visitors. Then when users browse to targeted merchants’ sites, the stealware programs jump into action, causing merchants’ tracking systems to think users reached the merchants thanks to the stealware programs’ efforts.
Stealware raises several major policy concerns. For one, merchants risk throwing away money — paying commissions when none are due, increasing their costs, and ultimately raising prices for everyone. For another, legitimate affiliates lose commissions when stealware programs overwrite their tracking codes with stealware programs’ own codes. Finally, stealware puts affiliate networks (like LinkShare and Commission Junction) in a truly odd position: If the networks enforce their rules and remove stealware programs from their networks, then the networks shrink and receive smaller payments from merchants.
I’ve begun my research in this field with a particular program that I believe to be the largest and most prevalent of those that specifically seek to add and replace affiliate commissions: Like Gator and WhenU, Zango (from 180solutions / MetricsDirect) monitors users’ activities and sometimes shows popup ads (though 180’s ads are particularly large, often covering the entire browser window). But the real news is that Zango frequently sets and replaces affiliate tracking codes — as to some 300+ major merchants, using at least 49 different affiliate accounts and scores of redirect servers.
Much of Zango’s affiliate code replacement lacks any on-screen display. As a result, ordinary users (not to mention merchants’ testing staff) are unlikely to notice what’s going on. Where possible, I’ve captured Zango’s behavior with screenshots and videos. As to the rest, I’ve used my trusty network monitor to inspect the raw transmissions passing over my Ethernet wire.
Details:
The Effect of 180solutions on Affiliate Commissions and Merchants
What Advertisers Use WhenU?
Ever wonder who advertises on WhenU? A few reporters have tried to figure this out but have been stymied: Few companies care to talk about their use of Claria or WhenU. (WSJ [paid registration required], BusinessWeek).
So I thought I’d put together a list of all of WhenU’s current advertisers — all the companies showing graphical ads (not just sponsored link text) on WhenU’s system. There are 234 distinct advertisers, by my count. The biggest advertisers (by advertisement count) are Priceline (51 ads), J.P. Morgan Chase (43), Casino On Net (37), Verizon (28), Orexis (24). Major advertisement categories:
| Gambling, Betting and Bingo | 327 advertisements | 49 advertisers |
| Loans | 263 advertisements | 35 advertisers |
| Travel | 213 advertisements | 21 advertisers |
Further down the list, 102 ads for insurance, 99 for sexual health (mostly Viagra and similar products) and even some ads for online psychics and online cigarette sales.
All the details, and thousands of advertisement thumbnails, are in:
Utah Spyware Control Act On Hold updated July 7, 2004
Today brought closing arguments in WhenU.com, Inc., v. The State of Utah.
After closing arguments, Judge Fratto granted WhenU’s Motion for Preliminary Injunction, enjoining current enforcement of the Spyware Control Act. Ruling from the bench, Judge Fratto stated that he was not persuaded that WhenU had satisfied the requirements of showing a substantial likelihood of prevailing on the merits of its constitutional challenge as to the spyware provisions of the Act, but that WhenU had satisfied such showing regarding the context-triggered pop-up ads provision. Nonetheless, Judge Fratto enjoined enforcement of the act in its entirety. See transcript of ruling.
For my perspective on the factual portion of the hearing, June 10-11, see Report from WhenU v Utah.