“VistaPrint is disciplined in operation … [VistaPrint’s] marketing [uses] highly analytically driven fact-based decision-making … [W]e manage those [marketing partners] tightly.”
– VistaPrint CEO Robert Keane in a January 2008 earnings call
For more than four years, I’ve been monitoring online advertising — alerting advertisers, ad networks, and the general public when ad spending finds its way to spyware vendors and when advertisers are getting cheated. (Examples: 1, 2, 3, 4, 5) Every day, my Automatic Spyware Tester browses the web on multiple spyware-infected PCs, watching for spyware-delivered advertising and recording its observations in videos and packet logs.
Although VistaPrint’s Robert Keane claims to effectively oversee VistaPrint’s marketing practices, I emphatically disagree. To the contrary, I’ve seen ample evidence of VistaPrint promoted by spyware and adware programs that sneak onto users’ computers without consent (including through security exploits) and through ruse and deception. In many instances, including as detailed in the examples that follow, the corresponding affiliates trick marketing analytics — claiming commission on sales that would have happened anyway, and thereby overstating the true effectiveness of their marketing efforts.
When VistaPrint is cheated by rogue marketing partners, the costs fall in the first instance to VistaPrint shareholders. Every dollar wasted on worthless advertising leaves that much less for corporate profits, and VistaPrint’s advertising budget is already strikingly large: In 2008, VistaPrint marketing consumed 31.9% of revenue (more than $125 million) while profits were just 9.9% ($39.7 million). Meanwhile, fraud against VistaPrint also harms the general public: Consumers suffer unwanted installations of spyware programs funded, in part, by theft from VistaPrint.
The following table summarizes my recent observations of fraud against VistaPrint:
| Ad network |
Example incident |
Rogue VistaPrint incidents observed |
| August – September 2008 |
January – July 2008 |
| Number of affiliates |
Number of dates |
Number of observations |
Number of observations |
| Lynxtrack |
Vomba, Hydra Network Affiliate 19934 |
6 |
13 |
18 |
32 |
| Clickbooth |
Vomba, Clickbooth Affiliate 14941
WhenU, MediaTraffic, Iadsdirect, Clickbooth Affiliate 7781 |
5 |
13 |
14 |
14 |
| CPA Builder (including traffic from Revenue Gateway, from OptInRealBig / CPAEmpire, and from XY7) |
Zango, Revenue Gateway Affiliate 12489, CPA Empire, CPA Builder |
2 |
8 |
9 |
21 |
| CX Digital Media (Incentaclick) |
Vomba, Weclub, CX Digital Media Affiliate 13736 |
2 |
2 |
2 |
18 |
| Performics (Google) |
Deluxe Communications, Smartyseek, Performics |
1 |
5 |
5 |
5 |
| direct relationships & other networks |
not yet tabulated in full – some examples on file
|
During August-September 2008, my AutoTester repeatedly observed VistaPrint facing rogue traffic coming from five different ad networks. In the sections that follow, this piece presents an example of fraud by an affiliate from each of the specified networks. But I’ve seen plenty more. My AutoTester has been running for more than a year — preserving tens of thousands of records of online advertising fraud, including 133 other spyware incidents arising out of traffic to VistaPrint. These many incidents confirm the breadth of improper practices by VistaPrint’s marketing partners.
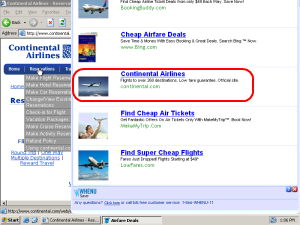
Example 1: Vomba, Hydra Network Affiliate 19934 Claiming Commission on VistaPrint’s Organic/Type-In Traffic
 Vomba, Hydra Network Affiliate 19334 Targeting VistaPrint
Vomba, Hydra Network Affiliate 19334 Targeting VistaPrint
In testing on September 12, my AutoTester browsed VistaPrint’s site on a computer with Vomba (from Integrated Search Technologies, makers of Slotchbar, XXXtoolbar, WhenU, AdVantage, and more). Vomba popped open a window that sent traffic to Hydra Network (LynxTrack) (affiliate 19934), and Hydra Network in turn forwarded the traffic back to VistaPrint. The result was the screen shown at right — the original VistaPrint window at left/back, with a new popup at front/right.
Crucially, both web browser windows share a single set of cookies. Whether the user buys from the original VistaPrint window or from the popup, cookies tell VistaPrint that this Hydra Network affiliate caused the sale. So VistaPrint will pay this affiliate a commission — even though, in fact, the affiliate did nothing whatsoever to facilitate the sale. I call this tactic “self-targeting” — reflecting that Vomba covers VistaPrint with its own ad. All of the examples presented on this page entail spyware/adware performing this kind of self-targeting attack.
My AutoTester preserved a video of this incident and a packet log of the underlying network traffic.
My AutoTester observed this same affiliate using the same method on three different dates in August-September 2008. My AutoTester also observed five other Hydra Network affiliates similarly defrauding VistaPrint. All told, in August-September, my AutoTester observed 18 such incidents on 13 distinct dates.
My AutoTester’s records indicate that Hydra Network receives substantial spyware-originating traffic. Looking back to June 2007, across all my AutoTester’s browsing, my AutoTester has seen a remarkable 1,287 instances of spyware sending traffic to/through Hydra Network.
Example 2: Vomba, Clickbooth Affiliate 14941 Claiming Commission on VistaPrint’s Organic/Type-In Traffic
In testing on September 12, my AutoTester browsed VistaPrint’s site, again on a computer with Vomba. Vomba popped open a window that sent traffic to Clickbooth (affiliate 14941), and Clickbooth in turn forwarded the traffic back to VistaPrint.
Because both web browser windows share a single set of cookies, this Clickbooth affiliate gets paid a commission whether the user buys from the original VistaPrint window or from the popup. This commission gets paid even though, in fact, the affiliate did nothing whatsoever to facilitate the sale.
My AutoTester preserved a video of this incident and a packet log of the underlying network traffic.
My AutoTester observed this same affiliate using the same tactics on eight different dates in August-September 2008. My AutoTester also observed three other Clickbooth affiliates similarly defrauding VistaPrint. All told, my AutoTester observed 13 such incidents on 12 distinct dates.
My AutoTester’s records indicate that Clickbooth receives substantial spyware-originating traffic. Looking back to June 2007, across all my AutoTester’s browsing, my AutoTester has seen 917 instances of spyware sending traffic to/through Clickbooth.
Example 3: WhenU, MediaTraffic, Iadsdirect, Clickbooth Affiliate 7781 Claiming Commission on VistaPrint’s Organic/Type-In Traffic
In manual testing on September 28, I browsed VistaPrint’s on a computer with WhenU. WhenU opened a popunder that flashed briefly on screen (video at 0:15) but then forced itself to an off-screen location where I could not see it even if I minimize other windows. (See video at 0:24 to 0:30, when I attempted to find the popunder.) By manually right-clicking and choosing “maximize,” I managed to make the popunder visible — confirming that it loaded VistaPrint and noting the affiliate ID number.
Packet log analysis reveals that traffic flowed from WhenU to MediaTraffic (a pay-per-view advertising marketplace also operated by Integrated Search Technologies) to Iadsdirect to Clickbooth (affiliate 7781) to VistaPrint.
As in prior examples, both windows share a single set of cookies. Thus, the WhenU popunder causes the corresponding affiliate to receive a commission if the user makes a purchase — even though the affiliate did nothing to encourage or facilitate a purchase.
I preserved a video of this incident and a packet log of the underlying network traffic.
This advertising fraud by WhenU is particularly notable because WhenU previously claimed to have reformed all unsavory practices. (See e.g. “WhenU CEO Bill Day Cleans House.”) Moreover, WhenU previously touted a TRUSTe Trusted Download certification, and TRUSTe specifically prohibits Trusted Download programs from defrauding advertisers. (See Certification Agreement, Schedule A (“Program Requirements”), provision 14.k.) That said, WhenU has silently left the Trusted Download whitelist. Furthermore, in separate testing of WhenU software, I have recently seen repeated self-targeting fraud improperly claiming commissions from a variety of advertisers.
Example 4: Zango, Revenue Gateway Affiliate 12489, CPA Empire, CPA Builder Claiming Commission on VistaPrint’s Organic/Type-In Traffic
The Money Trail and Traffic Flow
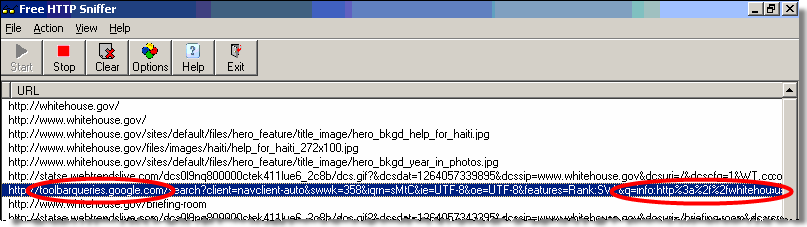
In testing on September 21, my AutoTester browsed VistaPrint’s site on a computer with Zango. Zango popped open a window that sent traffic to Revenue Gateway (affiliate 12489), which redirected to CPA Empire (formerly OptInRealBig), which redirected to CPA Builder, which in turn forwarded the traffic back to VistaPrint.
The chain of intermediaries adds additional complexity to the relationships. But traffic flows in a continuous forward path: From Zango to Revenue Gateway to CPA Empire to CPA Builder and finally back to VistaPrint. Conversely, revenue flows in the opposite direction: From VistaPrint to CPA Builder to CPA Empire to Revenue Gateway to Revenue Gateway affiliate 13425 to Zango. The diagram at right summarizes the flows of traffic and money.
My AutoTester preserved a video of this incident and a packet log of the underlying network traffic.
During August-September 2008, my AutoTester also observed other incidents wherein spyware waited for a user to browse the VistaPrint site, then sent the user back to VistaPrint via CPA Builder. Beyond this Zango / Revenue Gateway / CPA Empire example, I also observed incidents wherein CPA Empire’s relationship with XY7 was the source of the tainted traffic. All told, my AutoTester has preserved more than 600 incidents of spyware sending traffic to/through CPA Empire, as well as at least 24 incidents of spyware sending traffic to/through Revenue Gateway (though I have reason to believe that some Revenue Gateway incidents were not preserved).
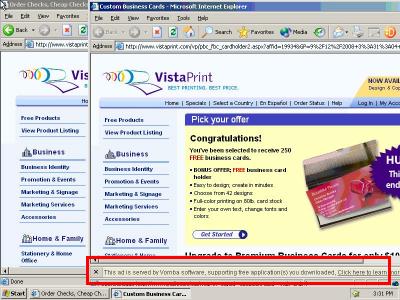
Example 5: 8/17/08 – Vomba, Weclub, CX Digital Media (Incentaclick) Affiliate 13736 Claiming Commission on VistaPrint’s Organic/Type-In Traffic
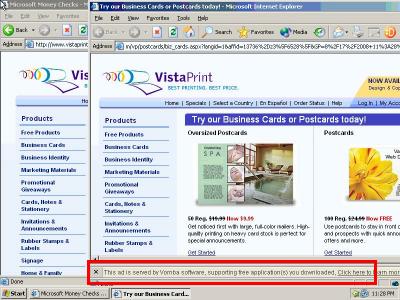 Vomba, Weclub, CX Digital Media Affiliate 13736 Targeting VistaPrint
Vomba, Weclub, CX Digital Media Affiliate 13736 Targeting VistaPrint
In testing on August 17, my AutoTester browsed VistaPrint’s site on a computer with Vomba. Vomba popped open a window that sent traffic to Weclub, which immediately redirected to CX Digital Media (Incentaclick), which in turn forwarded the traffic back to VistaPrint.
See the screenshot at right. My AutoTester preserved a video of this incident and a packet log of the underlying network traffic.
During August-September 2008, my AutoTester also observed another CX Digital Media affiliate using spyware to claim commission on VistaPrint’s organic traffic. All told, my AutoTester has preserved more than 200 different incidents of spyware sending traffic to/through CX Digital Media.
Example 6: Deluxe Communications, Smartyseek, Performics Claiming Commission on VistaPrint’s Organic/Type-In Traffic
In testing on September 14, my AutoTester browsed VistaPrint’s site on a computer Deluxe Communications (which I have repeatedly observed installed through security exploits and otherwise without user consent). Deluxe Communication popped open a window that sent traffic to Smartyseek, which immediately redirected to Performics, then back to VistaPrint.
In typical Deluxe Communications fashion, the popup window entirely covered the window the user had been browsing. But because both windows showed VistaPrint, some users might not notice.
My AutoTester preserved a video of this incident and a packet log of the underlying network traffic.
My AutoTester observed this same affiliate using the same tactics on five different dates in August-September 2008, and my AutoTester also observed Performics traffic during VistaPrint browsing on five other (prior) occasions.
Responsibility and Causation
It’s easy to present VistaPrint as perpetrator: VistaPrint fails to adequately oversee its marketing partners. As a result, VistaPrint’s advertising spending helps fund spyware and adware programs that sneak onto users’ PCs, with serious harms to performance, reliability, and privacy.
But I also see an important sense in which VistaPrint is a victim: VistaPrint’s marketing partners are defrauding VistaPrint by claiming commissions on sales they actually did nothing to cause. Such commissions are entirely wasted, yielding no bona fide marketing benefit to VistaPrint.
By all indications, VistaPrint faces significant difficulties in supervising its marketing partners. Yet other major retailers handle such challenges with greater success. For example, it is comparatively rare to see spyware or adware promoting, defrauding, or attempting to defraud Amazon — even though Amazon spends nearly three times as much on marketing as VistaPrint ($344 million to $125 million).
What could VistaPrint do differently? For one, I question VistaPrint’s choice of marketing partners: As the preceding statistics indicate, I have repeatedly and widely seen spyware and adware sending traffic to many of the partners VistaPrint works with. VistaPrint might face less fraud if it favored marketing partners with a track record of successful supervision of their affiliates.
More generally, an affiliate currently faces little real downside to attempting to defraud VistaPrint. If an affiliate gets caught cheating, VistaPrint will terminate that affiliate, but I see little indication that VistaPrint exacts any meaningful penalty to make the affiliate (or the network providing that affiliate) regret its transgression. In Deterring Online Advertising Fraud Through Optimal Payment in Arrears, I suggest a different approach — paying affiliates more slowly so that they face greater losses if they are found to be cheating. Alternatively, VistaPrint might sue affiliates it learns are cheaters, as in eBay v. Digital Point Solutions and Lands’ End v. Remy.
Yet Keane’s remarks (“highly analytically driven fact-based decision-making”) reveal that VistaPrint is at least attempting to supervise its marketing partners to optimize its spending. How, then, could VistaPrint end up facing so much fraud? I suspect VistaPrint’s analytics actually lead the company astray. Consider the tactics presented above, from the perspective of the information easily available to VistaPrint’s marketing staff. Because these affiliates target users who are already interested in VistaPrint, the affiliates’ conversion rates are likely to be well above average. Moreover, because these affiliates incur limited costs, they can accept payments far below what Google might require. Thus, VistaPrint’s staff are likely to assess these affiliates favorably — without realizing that the traffic at issue is traffic VistaPrint would otherwise have gotten for free. Put differently: Although VistaPrint’s measurements may be very precise, they’re inaccurate because VistaPrint misunderstands the sources of affiliates’ traffic.
In attempting to prevent such fraud, VistaPrint should also examine its ad networks’ incentives. Ad networks often mark up affiliates’ fees: For every dollar VistaPrint is slated to pay to a given affiliate, that affiliate’s network takes another (say) $0.20. As a result, ad networks have a clear incentive to tolerate rogue affiliates: Networks make money from each sale credited to an affiliate, so ejecting rogue affiliates would directly reduce the network’s earnings.
The Big Picture
Spyware-based advertising fraud extends far beyond VistaPrint. Most merchants operating affiliate, CPA, or other conversion-contingent programs face similar fraud. But VistaPrint is a large and, purportedly, sophisticated advertiser. So VistaPrint could appropriately lead by example.
I’m overdue to present further examples of spyware and adware continuing to defraud major merchants. Historically my articles have tended to emphasize the largest US affiliate networks — Commission Junction, LinkShare, Performics. But there’s plenty of fraud through smaller networks too, as well as through networks based outside the US. I’ll present additional examples later this fall.
In January, an Anti-Spyware Coalition workshop asked “Is adware dead?” Some panelists responded substantially in the affirmative. But my AutoTester indicates otherwise. I’m pleased to see that big advertisers no longer advertise directly with major adware vendors. Yet a chain of indirection — adware sending traffic to one ad network, which forwards to another, then finally to an advertiser — continues to promote top brands. Furthermore, spyware-delivered banner farms and ad-loaders are becoming increasingly widespread. This month I saw adware still promoting American Express, Apple, and AT&T — to name just a few of the A’s. There’s plenty of work left to be done.